Follow us on Telegram for the latest updates: https://t.me/mothershipsg
You may better know Xavier Lur as a lifestyle personality on Twitter, but the 28-year-old recently put up content that is quite different this time.
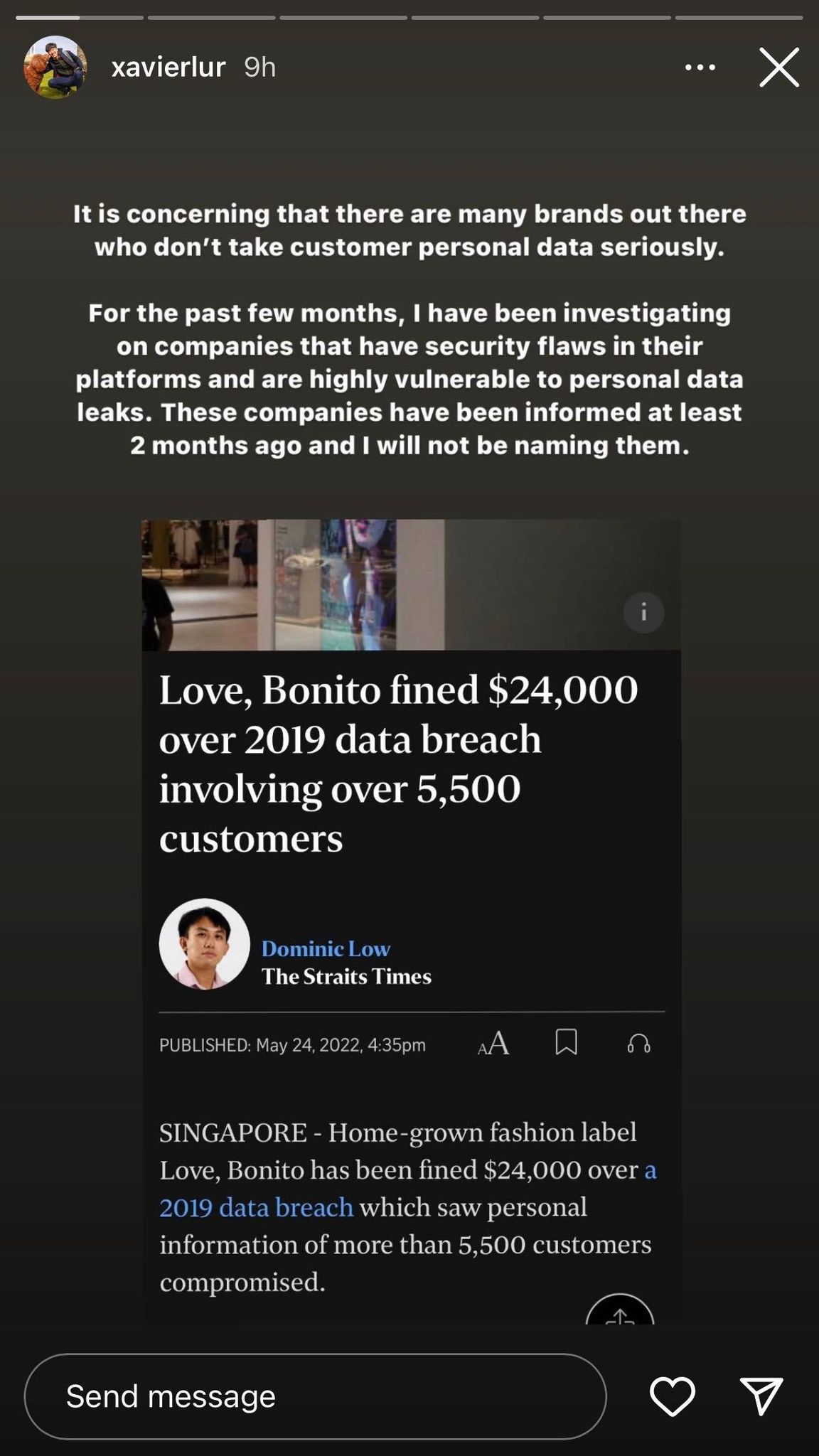
On May 28, 2022, Lur uploaded a series of Instagram Stories, detailing his successful attempts at extracting personal information from two companies.
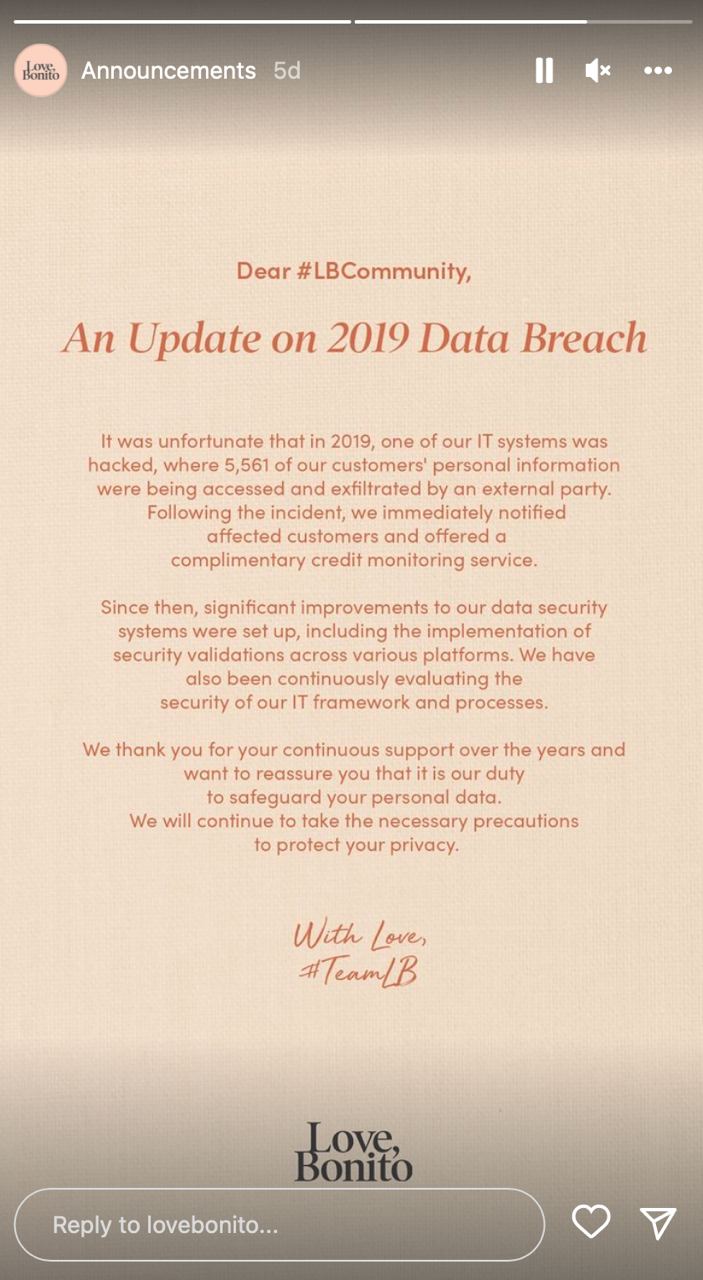
"It is concerning that there are many brands out there who don't take customer personal data seriously," he wrote, sharing an incident where local fashion label Love, Bonito had its customer information leaked after a malicious code was added to its website.
On May 24, 2022, about two years after the breach, the fashion brand updated customers that "significant improvements" have been made to their data security systems, in addition to a continual reevaluation of their IT frameworks and processes.
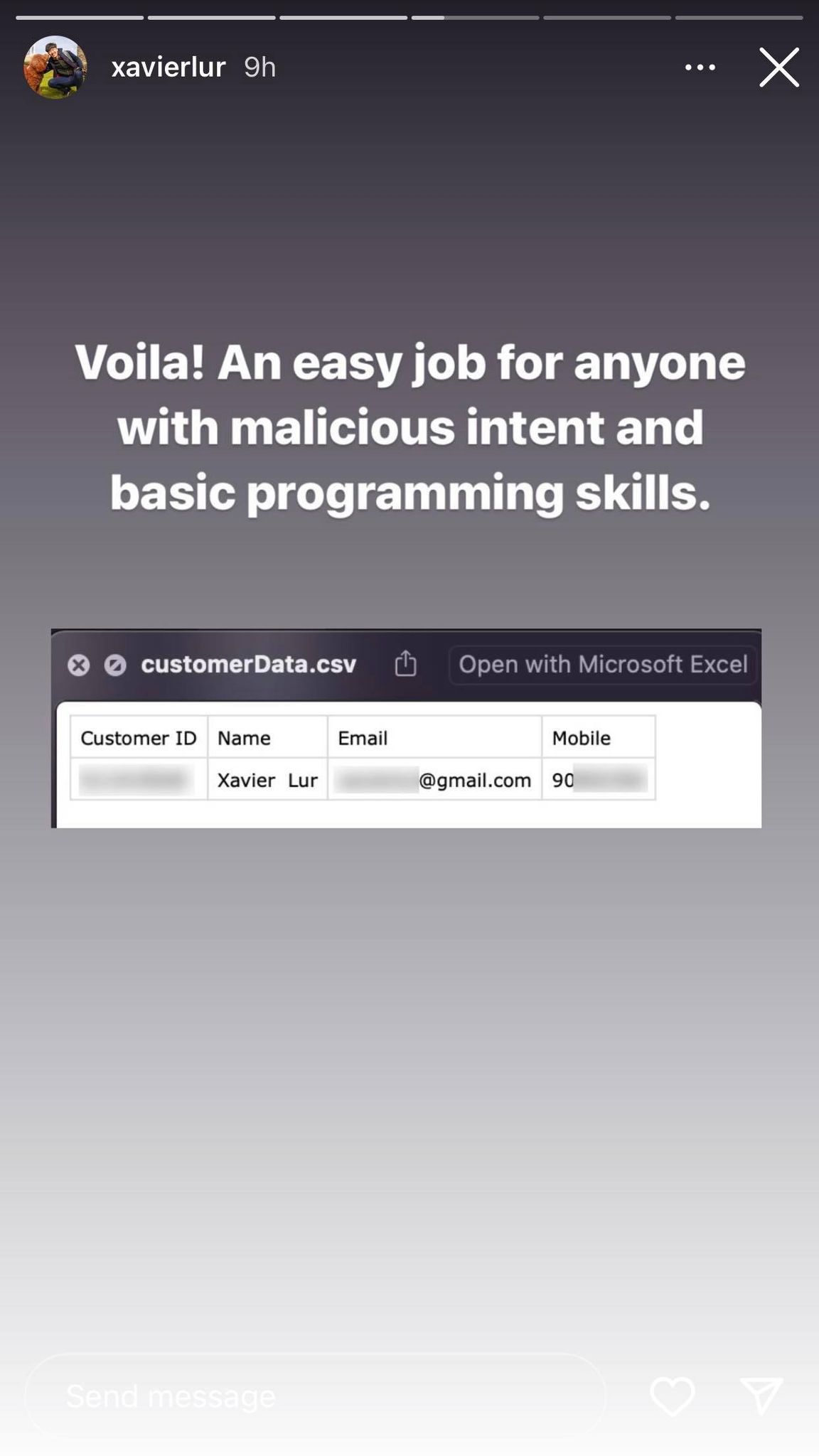
For the purpose of not landing himself in hot soup, Lur only retrieved his own information.
He added that the security loopholes have also been reported to the companies—which he will not be naming—two months ago.
In response to Mothership's query, Lur confirmed that neither of these companies are Love, Bonito.
Company A
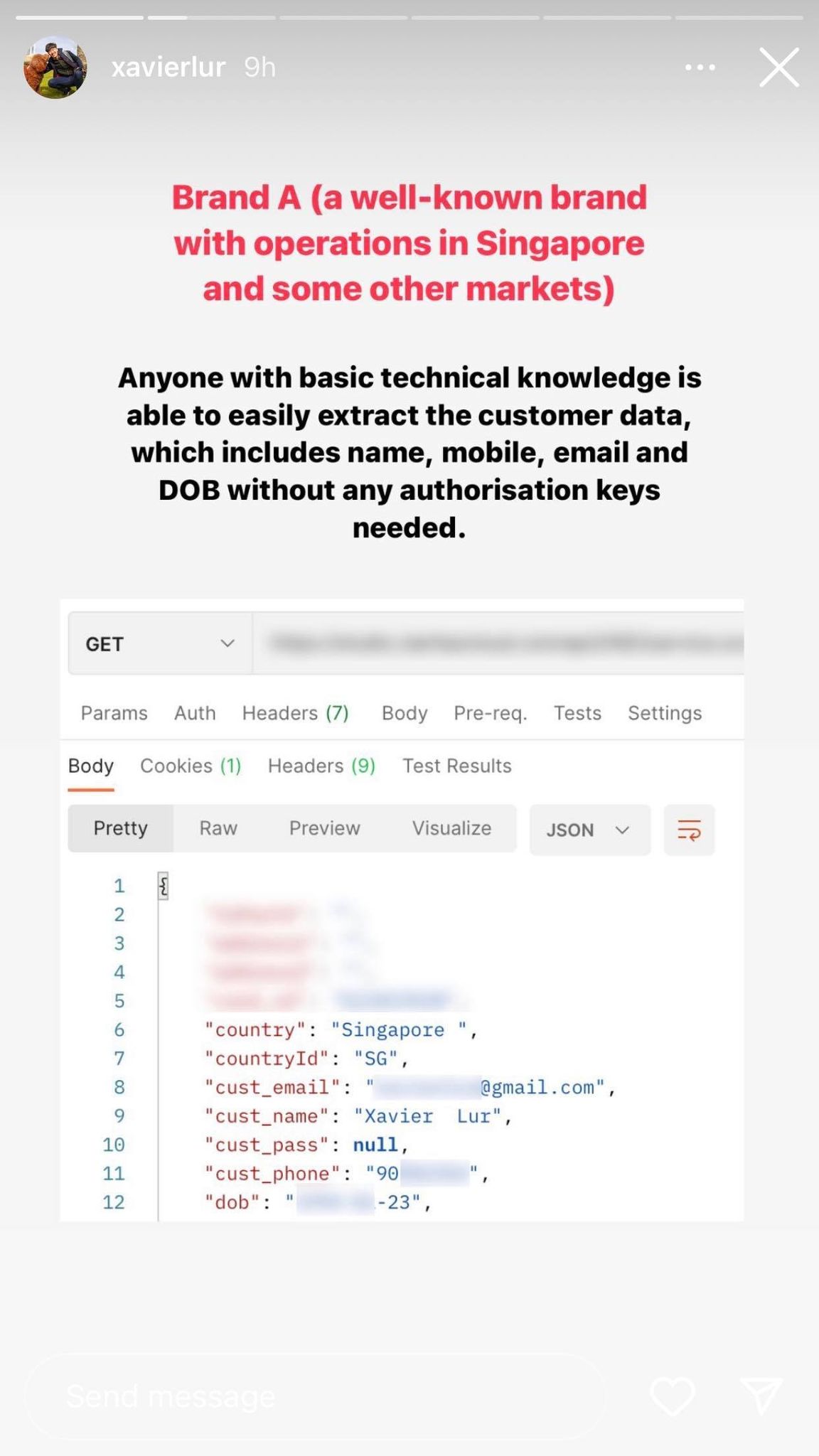
The first company that Lur "hacked" is a "well-known brand" with operations in both Singapore and overseas markets.
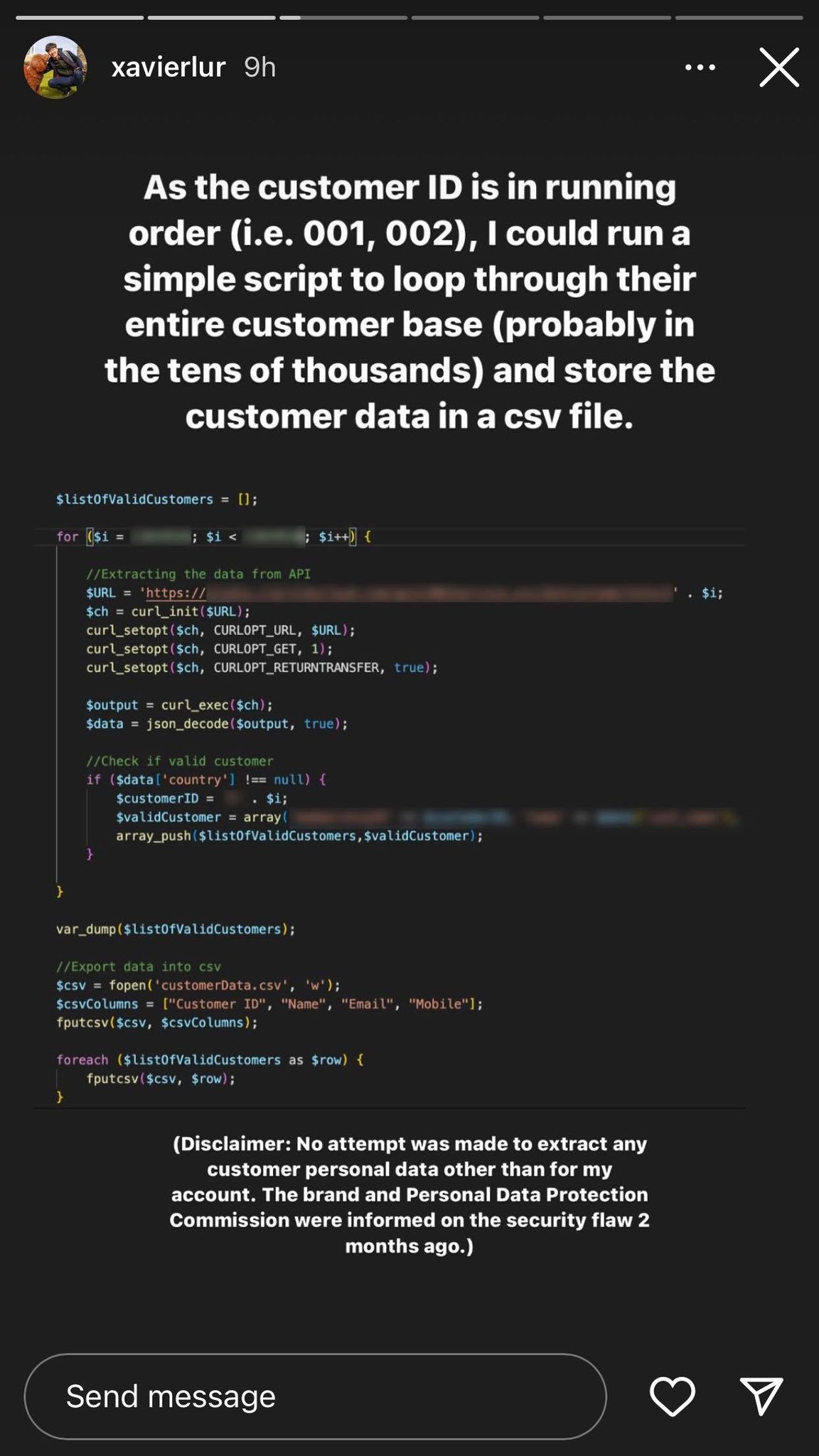
According to him, anyone with "basic technological knowledge" would have been able to access its customers' data, such as name, phone number, date of birth, and email.
A screenshot with Lur's personal information blurred out accompanied the Instagram Story.
It would also be possible to extract the entire database of customer information and store them in a file, although Lur did not attempt to do so.
Besides the company, the Personal Data Protection Commission (PDPC), Singapore’s "main authority" when it comes to personal data protection, has also been alerted to the security flaw.
Company B
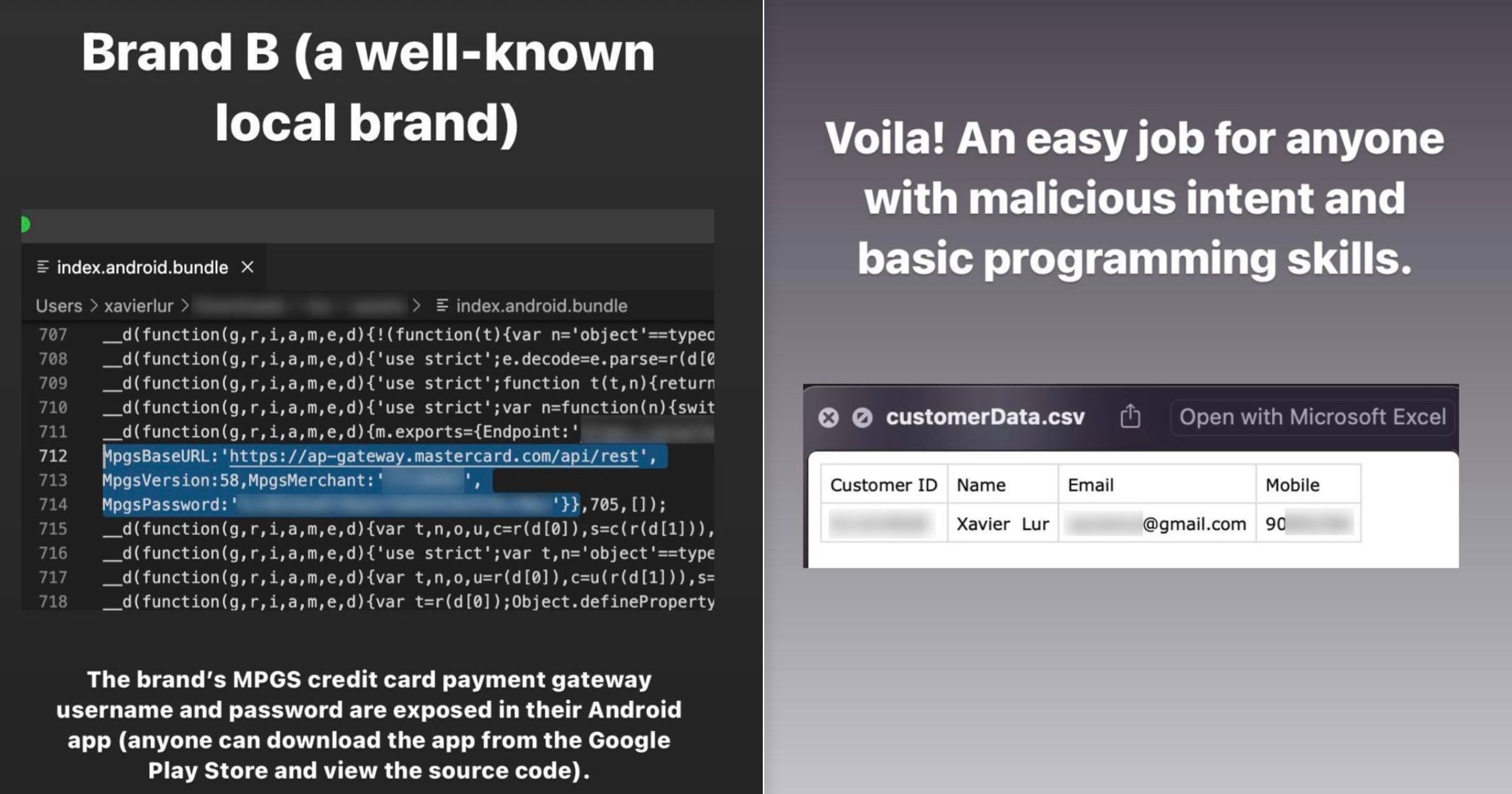
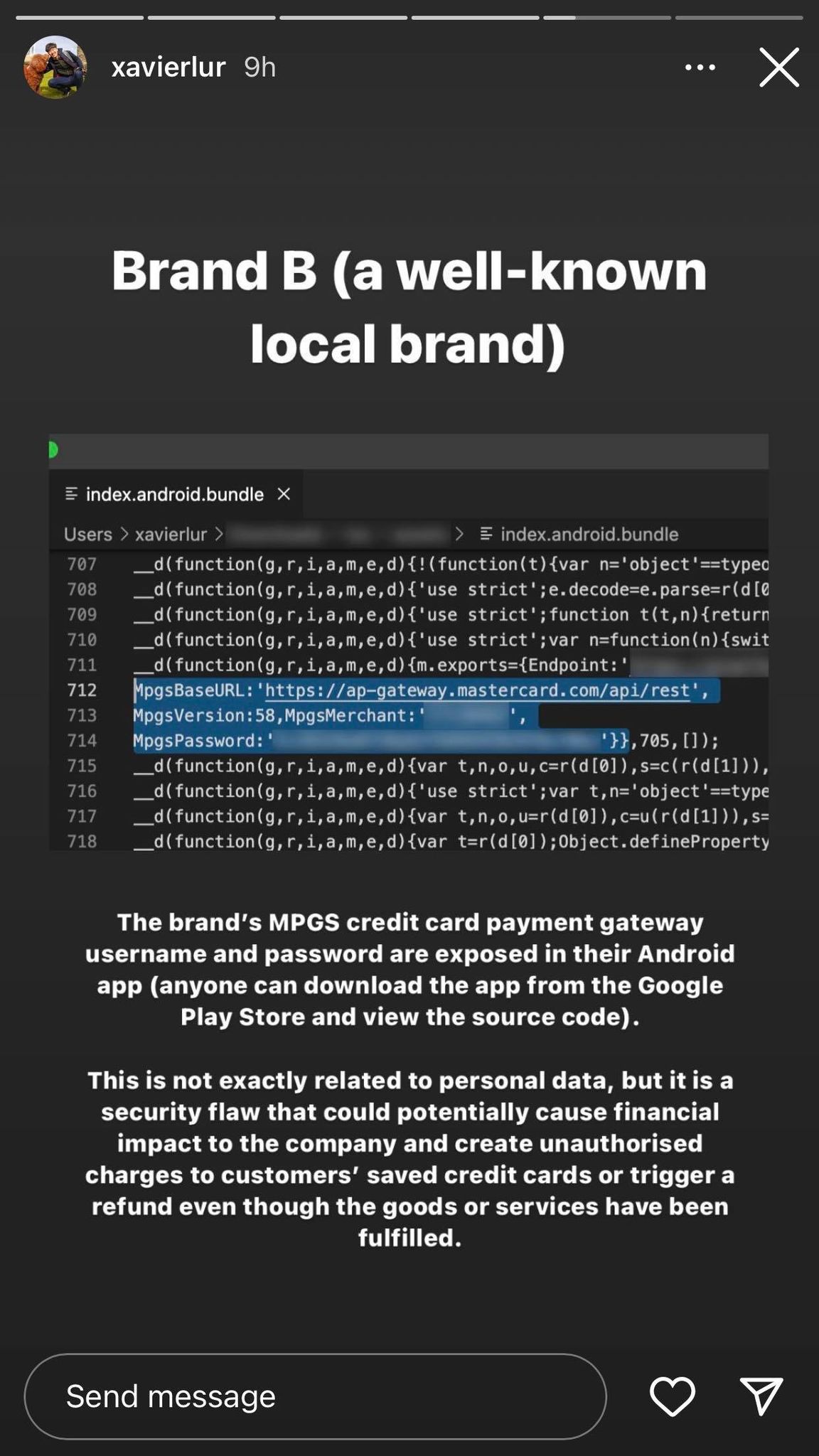
The second company that Lur acted on is also a "well-known local brand".
The case for this appears to be slightly more serious, as it pertains to financial side of things.
With the customers' MPGS' (Mastercard Payment Gateway Services) username and password exposed in the company's android app (which anyone can download), it is possible for several things to happen, as Lur illustrated with several examples.
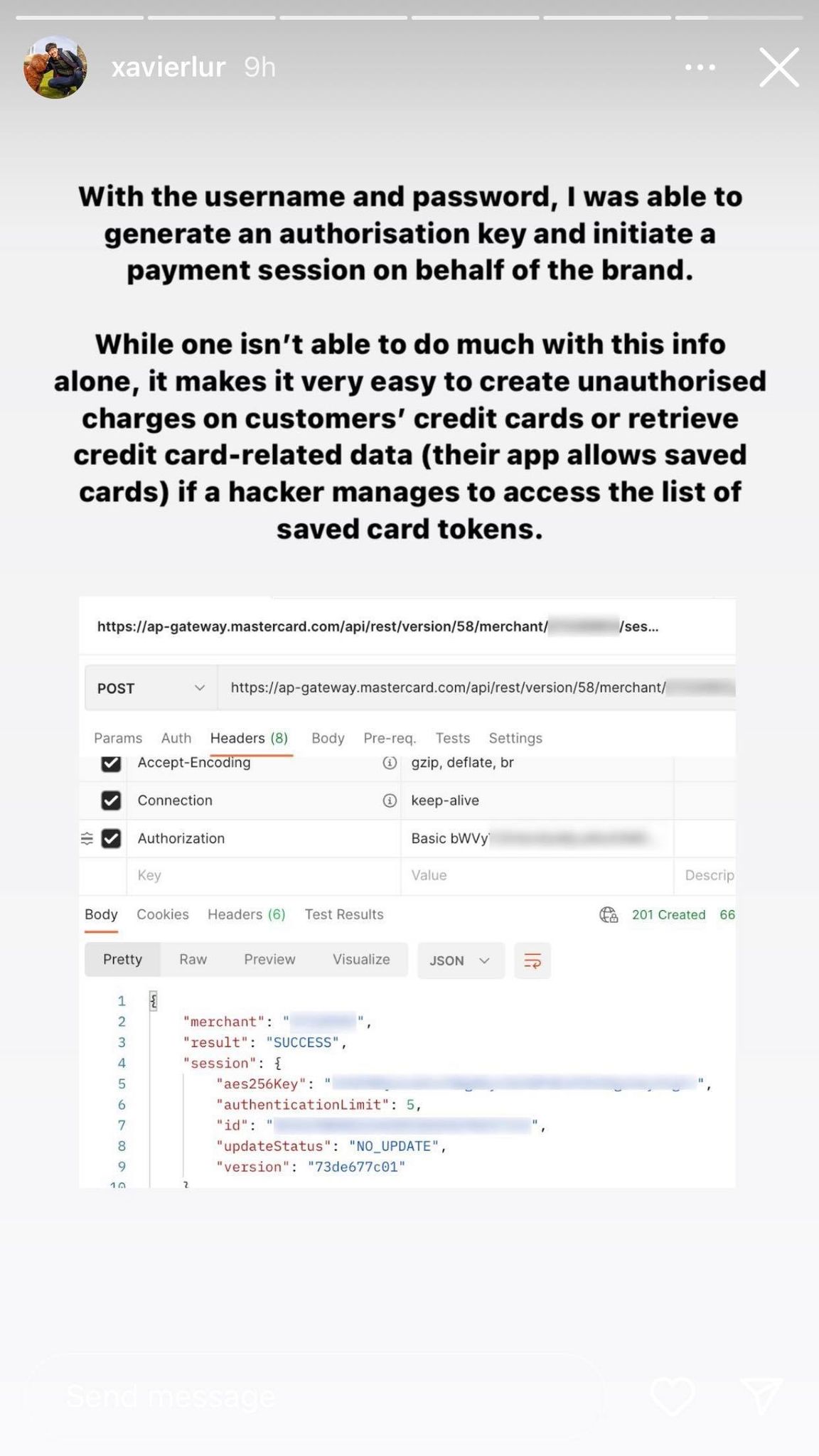
For instance, a hacker or third party could:
- Trigger unauthorised transactions using the customers' saved credit card
- Initiate a refund to the customer even when goods and services have been fulfilled by the company
- Retrieve credit card information from the saved token on the app
There is, however, the question of OTPs (one-time password), which Lur did not address in his Stories.
More susceptible to information loss than we realise
David Koh, the Chief Executive of Singapore’s Cyber Security Agency (CSA), previously explained how complacency may lead Singaporeans to conflate physical security and cybersecurity.
While Singapore is a relatively safe country to live in, one may "falsely [equate] our relatively good physical security with cybersecurity."
He made the additional observation that one knows immediately when they are a victim of crime in the physical domain, but may not realise right away that one's personal or even financial information has been stolen.
"We don't feel the impact directly to ourselves, because even when your data is 'lost', it's not lost, because you still have your data. The hacker has copied your data out."
In the physical domain, however, if you lose your wallet, you've lost it," Koh stated matter-of-factly.
Related article
Top image via Xavier Lur's Instagram page
If you like what you read, follow us on Facebook, Instagram, Twitter and Telegram to get the latest updates.