Follow us on Telegram for the latest updates: https://t.me/mothershipsg
In the final weeks of 2021, 469 OCBC customers lost S$8.5 million after falling victim to phishing scams.
Many of these victims lost their entire life savings.
OCBC has since agreed to make “full goodwill payouts” to those affected, and the Monetary Authority of Singapore (MAS) has followed up with a set of new measures to improve the security of internet banking.
As the dust starts to settle on the OCBC phishing scams, one pertinent question on everyone’s minds remain: Why was OCBC the target?
More specifically, was it simply OCBC's bad luck that they were the targets of these scams, and are the other banks equally at risk?
Or was there something about OCBC's security practices that made them an attractive target to scammers?
Mothership spoke to Aaron Ang, a cybersecurity expert and head of education services from ThriveDX SaaS, a digital education company, to find out how he thinks the scammers might have carried out their scheme.
How scammers know who to direct their phishing SMSes to?
Many of the victims recounted clicking on phishing links in messages sent in the same thread as their official OCBC messages.
Having these fraudulent messages appear on an “official” channel had convinced many that the messages were legitimate.
This was done via a method called “spoofing”, where a scammer - or anyone really - spoofs the SMS protocol by adding a “sender ID” field on SMS services.
But how are scammers able to know who to send these messages out to?
Ang said there are two possibilities -- one of which was simply mass sending these messages out to everyone with a Singapore phone number.
“In Singapore, there are only three main banks: DBS, UOB and OCBC. Chances are, most of us would have a DBS or OCBC account. Even if [the scammers] randomly send these messages out, it might hit someone with a DBS or OCBC account,” said Ang.
Another possibility Ang highlighted was that scammers had purchased these phone numbers off the dark web.
“There are actually a lot of sources that are available on the dark web that have what we call an 'info dump' or an 'accounts dump',” Ang said.
These “dumps” are collated lists of contact details that might have been leaked during previous phishing attempts.
Details such as phone numbers, names and email addresses can be sold to scammers for just a few hundred dollars, said Ang.
Scammers would presumably purchase these numbers and send targeted SMSes to these people.
Why was OCBC targeted?
Before suggesting why OCBC was seemingly the target of these scams, Ang said at this point, authorities are still investigating the scams, and that no one has a definitive answer as yet.
However, Ang said there were “a few things” that he could pick up that could lead one to deduce that “this was not just a random scam” but one that was “targeted” at OCBC.
Ang said the most discernible difference that sets OCBC apart from the other two local banks (DBS and UOB) was its procedure for setting up its digital banking tool – the OneToken.
According to victims, scammers were able to authorise transactions after gaining access into victims’ accounts and activating the OneToken.
DBS
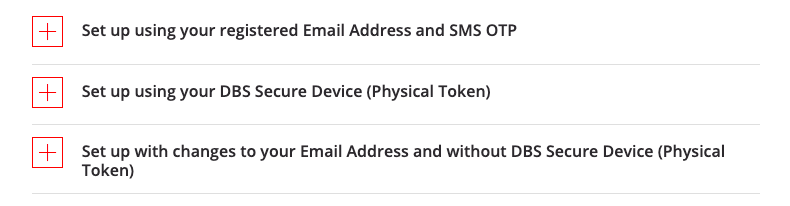
On its website, DBS lists three ways that its customers can set up its digital token.
 Screenshot via DBS wesbite.
Screenshot via DBS wesbite.
The first method requires the customer to log into the DBS iBanking app, and then input two different One-Time Passwords (OTP), one from a registered email address and another from SMS.
The other method requires one to log into the app, and then input an OTP into the physical token that the customer already owns.
The last method, for those without a physical token, requires an account login and a physical address where a code will be sent to after three to five working days. An SMS OTP is also required.
UOB
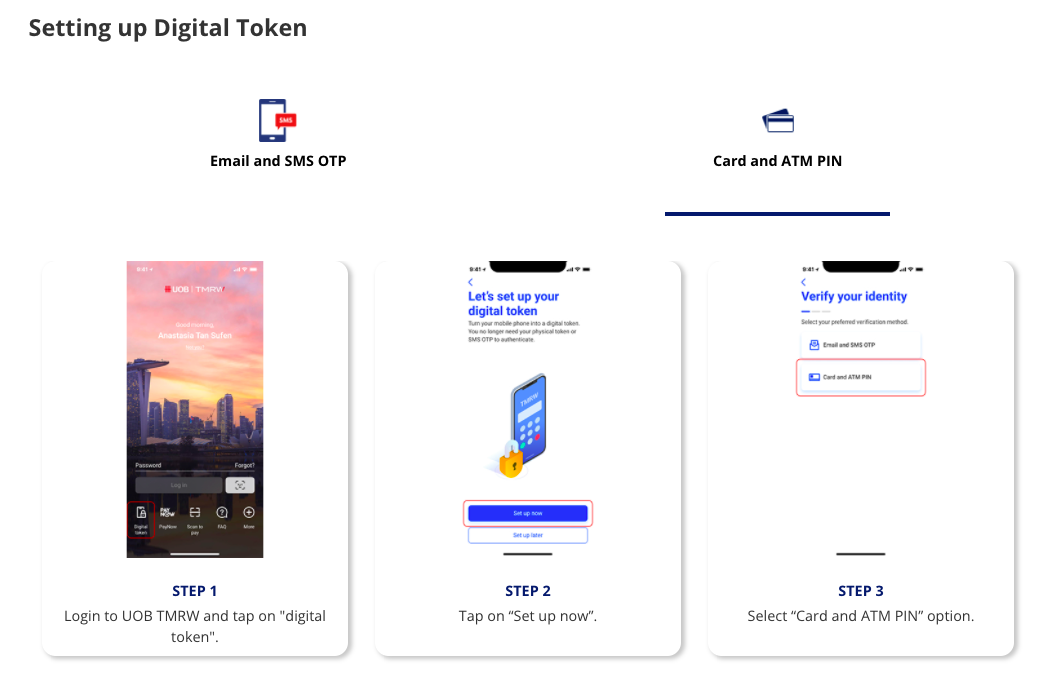
UOB offers two methods to set up its digital token.
 Screenshot via UOB website.
Screenshot via UOB website.
One method also requires both email and SMS OTP, but with an added two-minute waiting time for the digital token to be activated.
Another SMS OTP is needed after this waiting period.
The other method requires one’s card and ATM pin.
There is also a two-minute waiting period, and an SMS OTP that has to be imputed after the waiting period.
OCBC
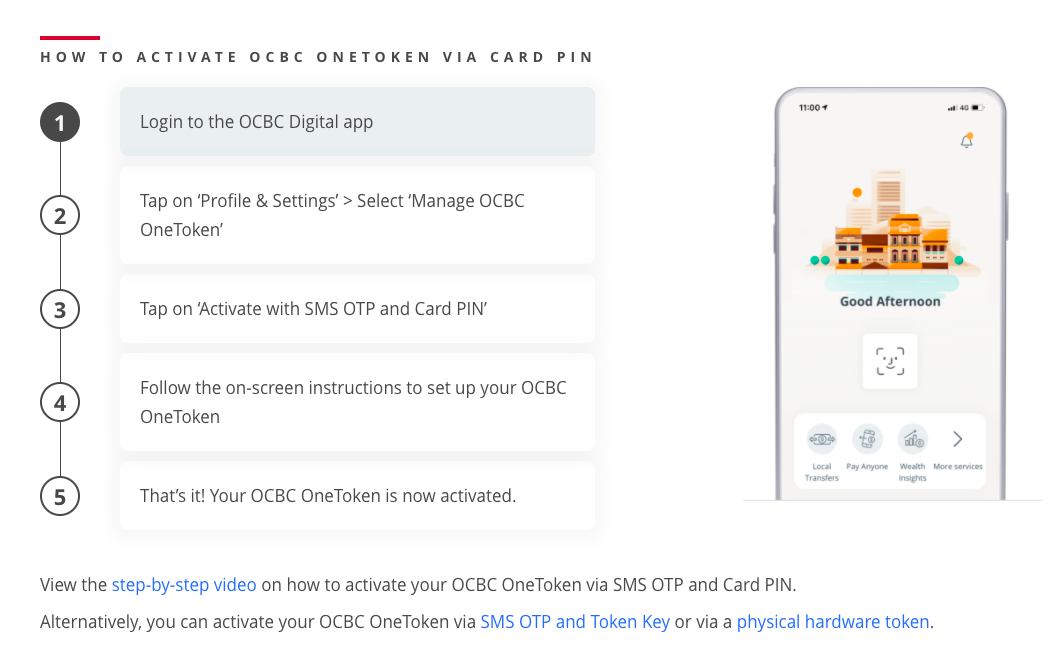
OCBC lists three methods to activate its OneToken.
 Screenshot via OCBC website.
Screenshot via OCBC website.
The one it primarily promotes on its website is by logging into one’s account and then entering a card pin and SMS OTP.
The other two methods are similar to the last two methods as DBS’s.
“If you compare the three banks, I would say, based solely on the instructions on the website, that OCBC is the lowest hanging fruit,” said Ang.
Ang shared that hackers have a mindset where they “always go for the path of least resistance or they go for the lowest hanging fruit”.
“If I’m thinking as a hacker, I want to maximise returns with the least possible resistance,” he added.
Comparing the digital token set-up instructions for each bank, DBS requires both email and SMS OTPs, and UOB has an additional two-minute waiting time where another OTP is required.
But OCBC lacks these additional security features.
“It’s the most convenient,” said Ang of OCBC’s OneToken set-up procedure.
Ang added that the scammers are likely not based locally, and are organised syndicates who are based overseas.
“The scammers can look up [the banks’] websites on how to set up the token, this will give them a sense of what they can do to bypass or circumvent some of these measures,” said Ang.
Putting himself in the shoes of a hacker, Ang said he “would go for OCBC”.
Ang, however, stressed that OCBC’s relatively “convenient” digital token set-up procedure which made OCBC an attractive target to scammers, was just a “possible reason” and may very well not be the “real reason” why scammers targeted the bank.
Since the spate of recent phishing scams, MAS on Jan. 19 announced that among new measures to enhance digital banking security, a delay of “at least 12 hours” will be required before a new soft token can be activated on a mobile device.
OCBC was just unlucky, other banks are “equally at risk”
Another cybersecurity expert, advocate at the ISC2 Singapore Chapter, Anthony Lim, had a different opinion.
“All the banks are equally at risk and it just happens that this time it was OCBC’s turn,” Lim said.
Lim pointed to past reports of DBS and UOB being targets of scams, albeit on a “much more limited scale”.
Lim said no matter the “success” that the scammers had with this recent heist, “they will not rest with one bank”.
They may turn their attention to other types of firms with online account services, such as retail securities trading or insurance companies.
He added that the recent scams may trigger other “copycat” attacks from other scammers, and said this may have already been done, referencing the recent IRAS and DBS scams that emerged after the wake of the OCBC scams.
Lim doubted that there was anything lacking in OCBC’s security practices, saying that the attacks did not manage to penetrate or compromise OCBC’s IT and security infrastructure, and that most banks had similar security practices for retail internet banking.
“To specifically target one bank may not necessarily yield the kind of ‘financial return’ success the scammers are looking for (unless they are not greedy),” Lim added.
Inputs from hard token should be required to set up soft token
Nonetheless, Ang said to improve security, banks should require that inputs from customers’ existing hard tokens be used when customers set up their soft (digital) tokens.
Currently, at all three banks, it is possible to activate the digital token without having to enter inputs from a hard token.
“If it’s so easy to change from the hard token to the soft token without entering the inputs from the hard token, something is wrong with this process,” said Ang.
He said requiring inputs from one’s existing hard token would prevent scammers from setting up digital tokens without the customer’s knowledge.
Ang, however, also recognised the trade-off that has to be made between convenience and security:
“If a person loses the hard token, or it’s out of battery, and therefore cannot add the OneToken, then the person wouldn’t be very happy, he would have to call the bank, or go down to the branch. These [inconveniences] would have to be taken into consideration as well.”
Change of mindset needed to combat scams
Ang called for a different approach in educating the public about scams:
“We need to actually educate people on the psychology of these scams, rather than just which action to take.
The tactics of the scammers will always be evolving.
We’ve been telling people ‘don’t click, don’t click’ [on links] for years. But people still click.”
Ang shared that the cybersecurity concept of “zero trust” can be useful as a guiding principle for the public to adopt:
“Zero trust means I don’t care if you’re my mum or my dad, I will always verify before I do something. So even if the request comes from a number that says ‘Mum’, and my ‘Mum’ is asking me for my username and banking password, I won’t trust it and will verify on my own why my mother is asking for such information.”
Ang also cautioned against a mentality that younger, more tech-savvy people might have, that they will never fall to scams.
“That kind of attitude is really dangerous, we all need to keep ourselves updated with what’s going on,” he said.
Lim similarly said that guarding against scams “goes back to the vigilance, skepticism, awareness and non-impatience of the user”.
Follow and listen to our podcast here
Top photo via Ming/Google Maps
If you like what you read, follow us on Facebook, Instagram, Twitter and Telegram to get the latest updates.
