Follow us on Telegram for the latest updates: https://t.me/mothershipsg
In the final two weeks of December 2021, at least 469 OCBC customers fell victim to phishing scams that saw a collective S$8.5 million swiped from their bank accounts.
While there have been many instances of phishing scams in Singapore, this latest round proved particularly devious, given the methods used and speed at which scammers were able to transfer funds out of victims’ accounts.
For many of the victims, however, the devastating loss of their hard-earned life savings was only made worse by what they perceived as a lackadaisical effort by the bank in helping them recover their funds.
A total of 10 victims who Mothership spoke to echoed similar sentiments that OCBC did little to help them remedy the situation, and expressed shock at how ill-equipped the bank was at handling scam cases.
Unable to get through hotline, money siphoned out while on hold
When 36-year-old homemaker, Denise (not her real name) and her husband realised that they may have been victims of a phishing scam, he immediately called the OCBC hotline to try to get the bank to stop the scammers in their tracks.
However, instead of getting a response, Denise’s husband was put on hold for over 20 minutes.
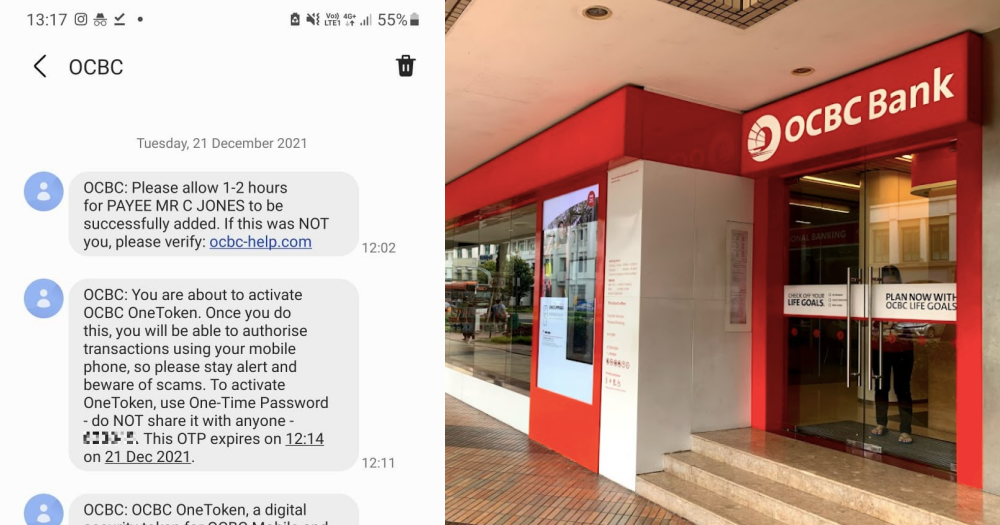
During which, he received more SMS notifications that his OneToken had been activated.
The OneToken is OCBC’s digital authentication tool for internet transactions.
He was also notified that his transaction limit was increased from S$5,000 to S$50,000.
Unable to get through, Denise’s husband carried on with his other tasks.
Two hours later, he received another SMS suddenly informing him that S$15,718 had been transferred out via PayNow.
Horrified, he called OCBC’s hotline again, but was put on hold. While waiting, he received an SMS that another S$2,400 had been transferred out.
By the time he got hold of an OCBC operator, he was informed that it was too late to do anything, since PayNow transactions are immediate.
He was told to make a police report.
“If OCBC had been more proactive, we would still have our money. Instead we were left waiting while the scammers were doing their work.” Denise said.
The couple was also baffled at how scammers were able to conduct so many high-risk activities with their account, such as changing transfer limits and setting up the OneToken, without ever giving out their one-time password (OTP).
Denise said this was revelatory and could indicate some systemic lapses in OCBC’s account security.
The OTP serves as a two-factor authentication process.
The couple claim they had only divulged their account login and password to the scammers after clicking on a phishing link sent via SMS through the OCBC message thread.
Many others that Mothership spoke to relayed their anger at not being able to get through the hotline when reporting scams, and questioned why there wasn’t a dedicated hotline for emergencies like these.
OCBC was “nonchalant”, had no sense of urgency
Two other women whom Mothership spoke to shared that they each had lost their entire life savings of about S$100,000.
Their experience trying to get answers or assistance from OCBC left them exasperated and disappointed.
When 38-year-old Kelly (not her real name) was trying to report her scam to OCBC, she said the hotline operator did not appear fussed at all when she informed them that over S$100,000 had been transferred out to an account in the UK.
Kelly, a senior manager, recounted her experience with the OCBC operator:
“The operator was nonchalant, she told me I had to fill up a feedback form and to make a police report.
I was so surprised that this was their response to such serious fraudulent cases. It was very underwhelming.”
When Kelly called the next day to get updates on her case, she found out that OCBC had not made any progress.
Actions that she thought OCBC would take, such as removing the scammer’s phone number from her account, were not done.
Going down to the main OCBC branch at Chulia Street for more answers was not any better, said Kelly.
After informing a queue assistant there that she had been a victim of a scam, she was only told to join the general queue and to wait for her number to be called.
This was in stark contrast to the response she received when she visited UOB and DBS branches the same day to check on her other accounts.
She was immediately brought to see the respective branch managers after staff there learnt about what had happened to her OCBC account.
OCBC staff was also slow to update Kelly on the status of her funds and their investigations.
It was only days later was she finally informed that her S$100,000 had been credited to the beneficiary’s bank account in the UK with no other explanation on what OCBC had done to prevent this from happening.
Her heart sank.
Kelly also bemoaned the fact that OCBC management has not expressed any responsibility or released any public statement on her matter, as well as on the recovery process.
She was scammed on Dec. 23.
OCBC did release a statement on Dec. 24 warning of phishing scams.
The whole ordeal has left Kelly shaken, and made her question if she can trust OCBC:
“In a safe country like Singapore, this is the first time I really feel vulnerable. There is some really serious, unethical corporate behaviour here. They are bullying everyday people, like you and me.”
Slow responses, missed deadlines
Sarah (not her real name), who is in her late 30s, shared with Mothership that save for S$60, her account had been wiped of S$98,000, and a further S$6,000 in cash advance payments to her credit card.
This was all the money she had been saving for years, set aside diligently for an emergency fund and to pay for her parents’ retirement.
Sarah relayed how she also was put on hold on the OCBC hotline as scammers infiltrated her account to change transfer limits and transfer money out.
“I felt so helpless, I knew something was happening but nobody could help to stop. If they answered much earlier, they could have stopped it,” she said.
Sarah said OCBC has not provided her any substantial updates on what happened to her money or the status of their investigations.
Instead, they only called her to tell her that they needed more time.
“They don’t seem to bear any responsibility for your loss. They just tell you that we need to give them more time to investigate. But from there, you know what kind of result they will tell you – it’s not favourable, from their tone or how they reply you,” she said through muffled sobs in her interview with Mothership.
Natalie (not her real name), 27, who works in the tech industry, said she was scammed of S$43,000 and another S$7,000 that was borrowed by the scammers using OCBC’s EasiCredit scheme.
When Natalie kept calling OCBC for updates, no one was able to give her any answers.
She said this was frustrating for her as her money had been transferred out via an overseas transfer, which would typically take a few days to reach the recipient.
“They couldn’t tell me whether the money was still with OCBC or not. I got different answers each time I asked,” said Natalie.
She added that each time OCBC gave her a self-imposed deadline, they were unable to meet it.
“They said, give us nine working days, we waited and nothing came back. Now they say 25 to 50 working days, I don’t know if [they] will come back. It’s endless waiting,” she said.
OCBC has also not answered her questions on whether the bank can waive the S$7,000 the scammers had borrowed using her account. She fears that OCBC would make victims pay for the money they did not borrow.
Natalie said while she has been a customer at OCBC for over four years, this experience has “proved” to her that OCBC lacks customer service, security control, and if a similar incident were to happen again, “they would not protect you”.
“I was a conscious saver and I've never had so little money in my account since I was 12. The scammers ruined me, and OCBC let it happen,” said Natalie, who added that she had planned for her money to go to her ageing parents.
Victims blame OCBC for being negligent
Most of the victims had clicked phishing links from SMSes that were spoofed to look like they came from OCBC, with the messages appearing in the same chat history as official OCBC messages.
Timothy (not his real name) and his wife, a couple in their late-20s who work in the e-commerce and hospitality industries respectively, had lost over S$100,000 to scammers.
Timothy said the SMS channel that was used to authenticate authorised transactions “can and has been compromised”.
“If OCBC knew beforehand, they should have taken efforts to secure or disable such a compromised channel. If not, it could mean severe negligence on their part,” he said.
Other victims Mothership spoke to said that they felt slighted by OCBC’s public messaging that alluded that they were fools for falling for such scams, as OCBC claimed they had consistently reminded its customers not to click on suspicious links.
Some pointed out that OCBC had previously sent marketing messages with links via SMS, and that they had been conditioned to click on such links.
OCBC said as of Jan. 4, 2022, they have ceased sending such links in light of the phishing scams.
Timothy, who started a support group for victims of the scams in December, said that there are still new victims, with some reporting that they were scammed as late as January 2022.
One daughter of a scam victim, who lost S$2,300, said that she was shocked that nothing substantial has been done to stop the scams from happening:
“Shouldn’t this sound an alarm to OCBC?
From the very first day that OCBC knew this was happening, [they] shouldn’t just be sending SMSes to warn customers, they should have totally disabled internet banking until they find out what is going on.
I know it would be a huge embarrassment for them, but at the end of the day, people would praise them for taking the proper action.”
Expert: Possible for scammers to access account without victim providing OTP
Cybersecurity expert and advocate at the ISC2 Singapore Chapter, Anthony Lim, explained how scammers might have been able to access victims' accounts seemingly without an OTP.
An OTP, or some form of two-factor authentication, is definitely needed to access certain features in one's account, but "with the requisite skill sets, technology, resources and motivation, scammers may be able to access a copy of the OTP that the bank sends out to its customers, and use that to make further access into victims' accounts," said Lim.
Lim said this did not mean that the telcos' or bank's systems were attacked or compromised, but that the scammers had their own IT equipment, software and communication services to attack the victims with.
He recommends banks consider a soft token application for two-factor authentication, but added that a downside to this method is that it would make it difficult for those "who aren't as tech-savvy".
When asked how the scammers were able to conduct such high-risk actions, such as changing transfer limits, making overseas transfers, and adding new payees over a very short period of time, Lim said that "this is indeed quite puzzling".
He said: "Banks typically have some processes which can be quite ‘inconvenient’ to change transfer limits unless they are relatively ‘small’ (e.g. below $20,000), or adding new payees."
But he added this may have been possible if the victims were "high-net worth individuals and already had high transfer limits", so making such large transactions "would not necessarily raise any red flags to the bank".
Heat turns towards telcos as well
In a Business Times article, "Fake SMS scams: Do banks and telcos have a duty of care to customers?" on Jan. 13, it was written that "attention is also turning to the role of the telcos in masking the identities of senders in the first place".
The article looked at the role SMSes play in getting victims to be phished in the first place as they enter fraudulent websites via seemingly mundane short messages sent to mobile devices.
Essentially, the BT piece wrote: "In theory, this means nearly anyone can impersonate a bank."
This was so as "number-masking technology can also be used by scammers to replace any phone number with an alphanumeric "spoofed header" or sender IDs -- most commonly the name of the bank".
Such a retracing of whose responsibility it is when phishing attacks happen sheds light on the lack of sophistication of unauthorised takeovers of victims' bank accounts, as no IT network or infrastructure has to be hacked or compromised.
And this is not the only take on who is to blame.
Phishing problem a shared responsibility
Bryan Tan, a technology and fintech partner at law firm Pinsent Masons and a former Singapore chapter president of the Internet Society, wrote in an opinion piece on CNA on Jan. 10 stating his view that the phishing problem is a shared responsibility.
Such a view absolves the bank of almost all responsibility as "the bank’s defence perimeter and security systems were secured" throughout the scam, Tan noted.
What the scams did do successfully is "employ a variety of social engineering tools and techniques to trick people into handing over their login information".
Moreover, Tan wrote: "The SMSes in question and the fraudulent website all operate outside of the bank’s systems."
This view naturally concludes that the weakest link was the customer who fell for the ruse, while the bank simply operated as it should have if the transactions were genuine and not part of a scam.
Trying to pin the blame on the bank might also be a tall order, as Tan wrote that no reported cases have been brought to the courts based on a breach of the Technology Risks Management (TRM) guidelines, which was introduced by the Monetary Authority of Singapore (MAS) in 2002.
But that is also because TRM guidelines do not form the basis on which legal liabilities are determined, Tan added.
As it stands, with the phishing scams gaining national attention, the focus now appears to be on deciding whether systems outside of the bank need monitoring and what level of monitoring is appropriate.
OCBC’s response
In response to Mothership's queries, OCBC's head of group corporate security, Francisco Celio said:
"We understand and share the anxiety of our customers who have fallen prey to this recent SMS phishing scam which impersonated OCBC and preyed on the fears of consumers about their personal bank accounts.
We have set up a dedicated team to help our affected customers through this difficult period. We have also contacted all the affected customers and are rendering assistance to them.
This SMS phishing scam is particularly aggressive and highly sophisticated in duping consumers into disclosing their personal banking details to fake websites despite repeated warnings from the bank to be alert and not to do so.
The use of the digital soft token or hard token for two-factor authentication is effective as an added layer of protection to access codes and PINs for logging in to a bank account. While most customers use the digital soft token, based on customers’ feedback, the hard token continues to be available.
Our first-level investigation into this particular SMS phishing scam has revealed that victims who had fallen prey had unknowingly provided their bank account information and internet banking login credentials, including SMS OTPs, to fake websites. This allowed scammers to take over their accounts and the scammers were then able to make fraudulent transactions in the guise of the customer.
Investigations into each report of this particular SMS phishing scam is complex and involves multiple checks, parties and systems. We seek our customers’ understanding to allow us to review every case very carefully and fairly. We will contact the affected customers again as soon as the investigation and review is complete."
Follow and listen to our podcast here
Top photo via Mothership reader and Marcus Woon/Google Maps
If you like what you read, follow us on Facebook, Instagram, Twitter and Telegram to get the latest updates.