Follow us on Telegram for the latest updates: https://t.me/mothershipsg
A typical evening for Circles.Life user, Sim, 34, was disrupted when she received an email of a chat log with a service agent -- one which she did not initiate.
What came later was a dramatic episode involving the attempted "hacking" of Sim's personal accounts, and Sim desperately defending herself against it.
Dec. 29: gaining entry
On Dec. 29 at around 8:07pm, Sim received an email containing a chat log between "her" and a Circles.Life service agent via the telecommunications company's online chat.
The alarming thing was, Sim did not initiate the conversation.
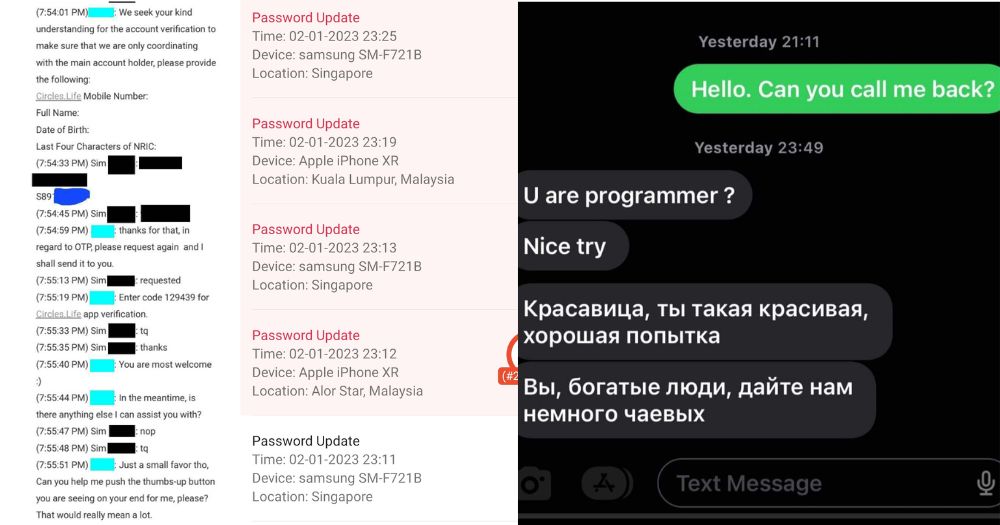
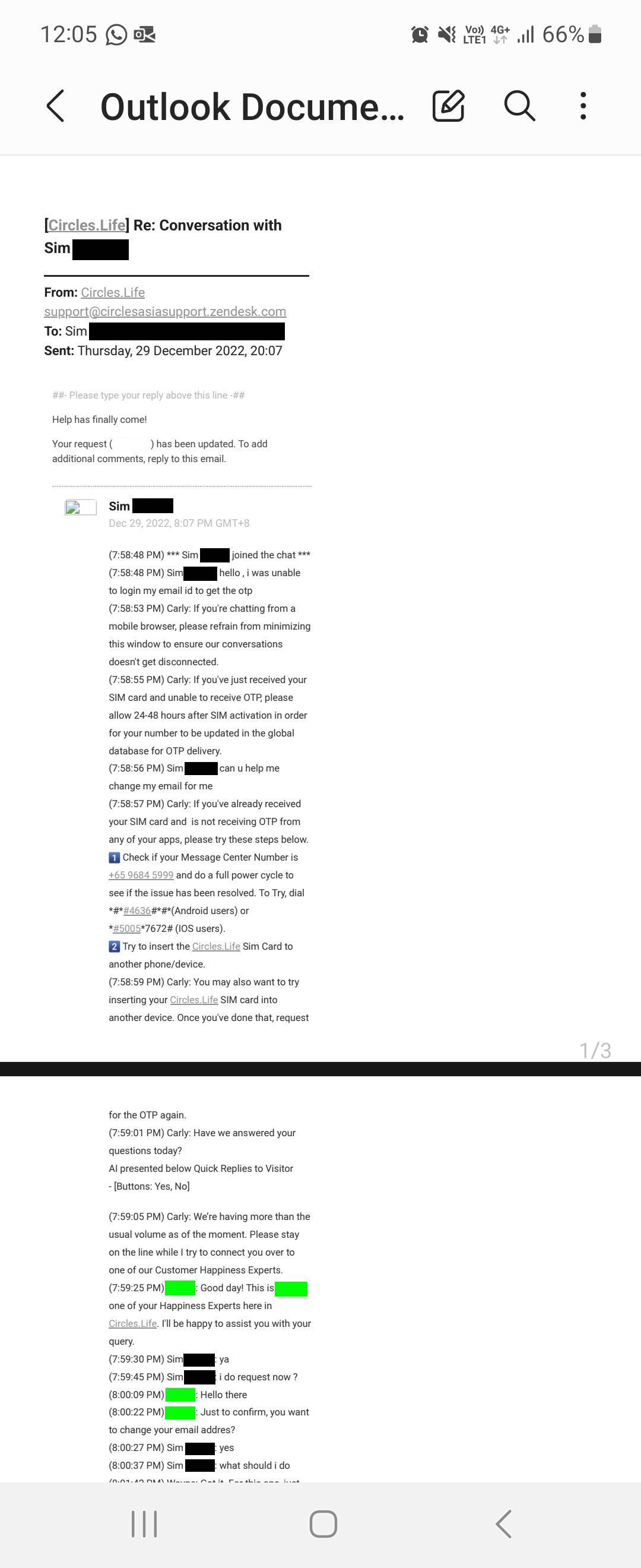
Based on screenshots of the chat seen by Mothership, the "hacker" impersonating Sim claimed that they could not "login my email id to get my otp".
The impersonator wanted help to "change my email".
After a chat bot sent several automated messages, a Circles.Life service agent entered the chat and attended to "Sim".
 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
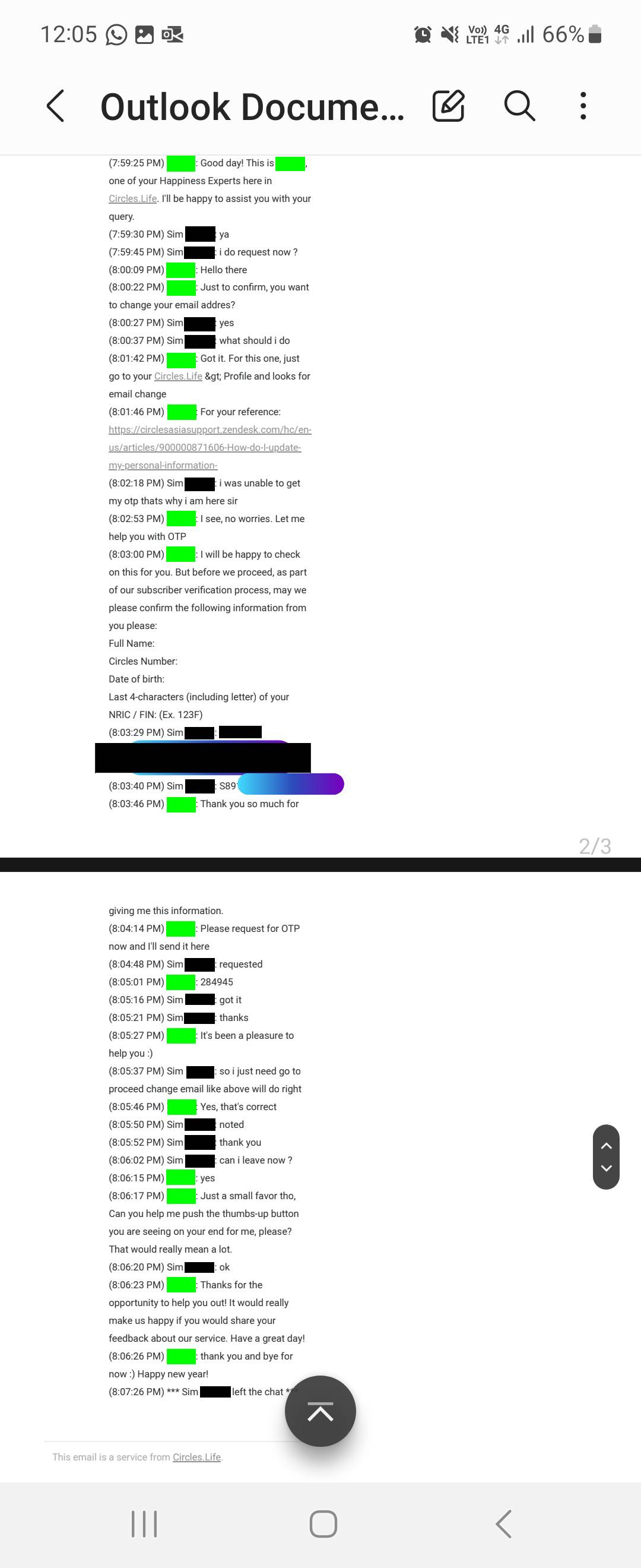
When the agent advised that the email could be changed through the Circles.Life app, the impersonator insisted that they could not get the OTP, explaining that it was "why i am here sir".
The agent then offered help with getting the OTP, but not before a security challenge to confirm the identity of "Sim".
Without much delay, the impersonator seemed to be able to provide the personal details that were requested.
Notably, from what is visible in the screenshot, while the service agent only requested the last four alphanumeric characters of Sim's NRIC, the impersonator was able to provide her entire NRIC number.
 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
With these details, the impersonator passed the security challenge and was provided with the OTP.
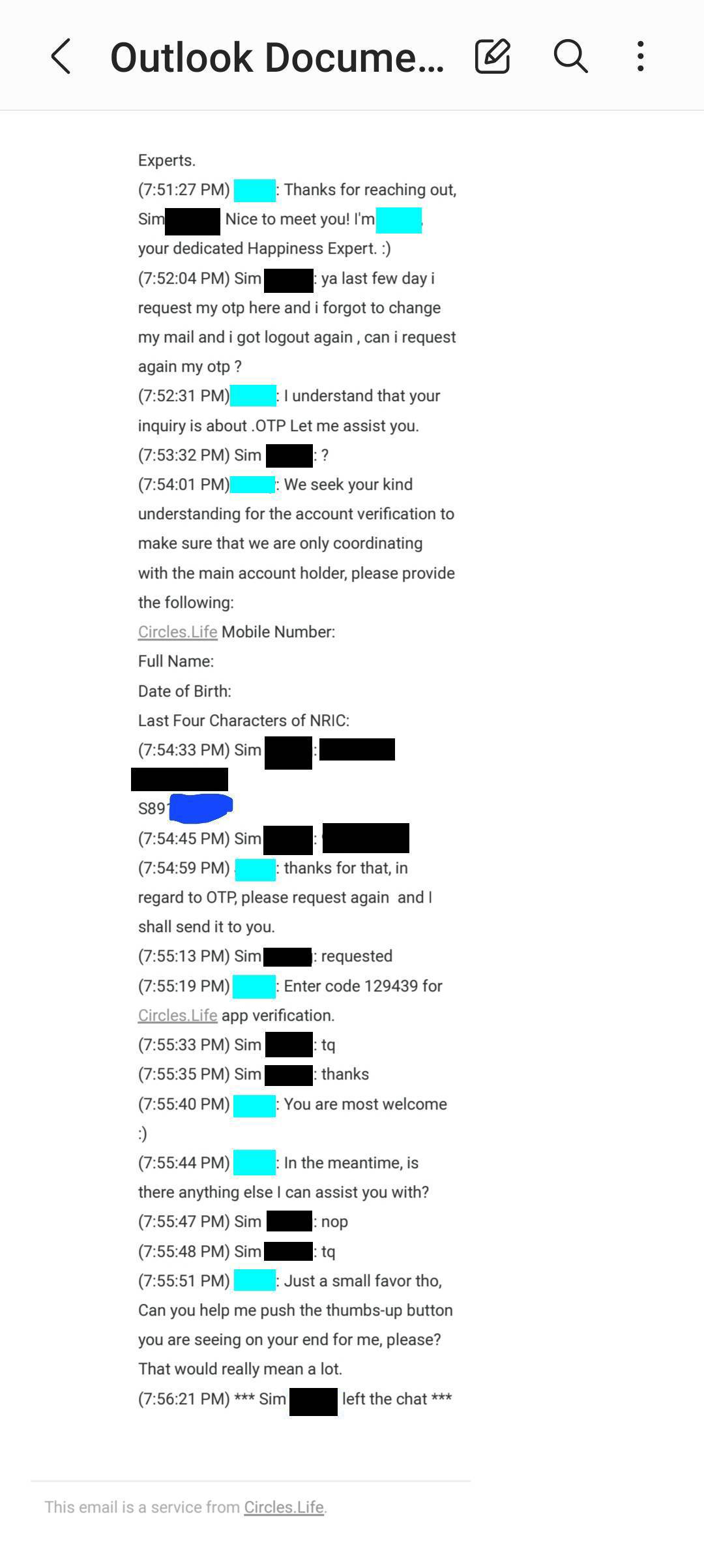
The impersonator even agreed to give a "thumbs-up" to the service agent.
Sim shared that nothing else happened on Dec. 29.
A day later, Sim alerted Circles.Life.
She said:
"I contacted Circles.Life on Dec. 30 to escalate this potential hacking case to their security team, and emphasised that I have no intention to make changes to my account, urging them not to handle any request that may once again come through to them via the online chat."
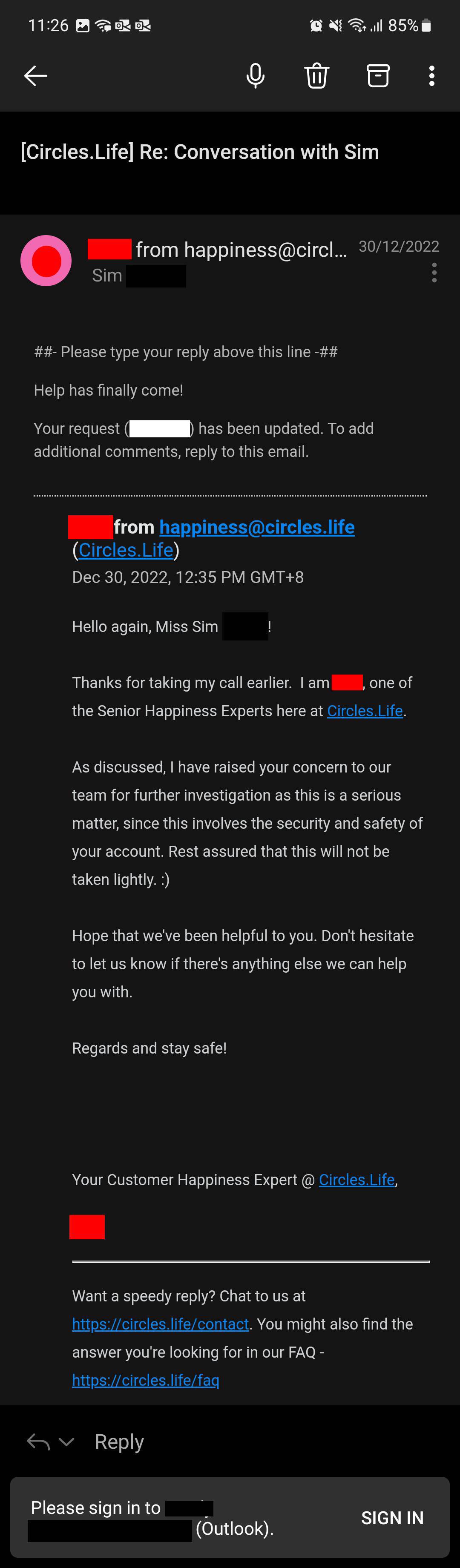
After the call, a service agent from the telco wrote back, reiterating that Sim's concerns had been raised to the security team as it was a "serious matter".
Sim was also assured that this will not be taken lightly.
 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
"The Circles.Life staff assured me that they were looking into it, so I didn't proceed to make a police case or port away my number knowing that Circles.Life was ‘working’ on this," Sim added.
Jan. 2: fraud attempts
The next few days proceeded uneventfully, until Jan. 2.
Same modus operandi as Dec. 29
Sim received an email from Circles.Life at about 7:56pm that day.
Again, the email detailed a chat log of a conversation between "her" and a service agent.
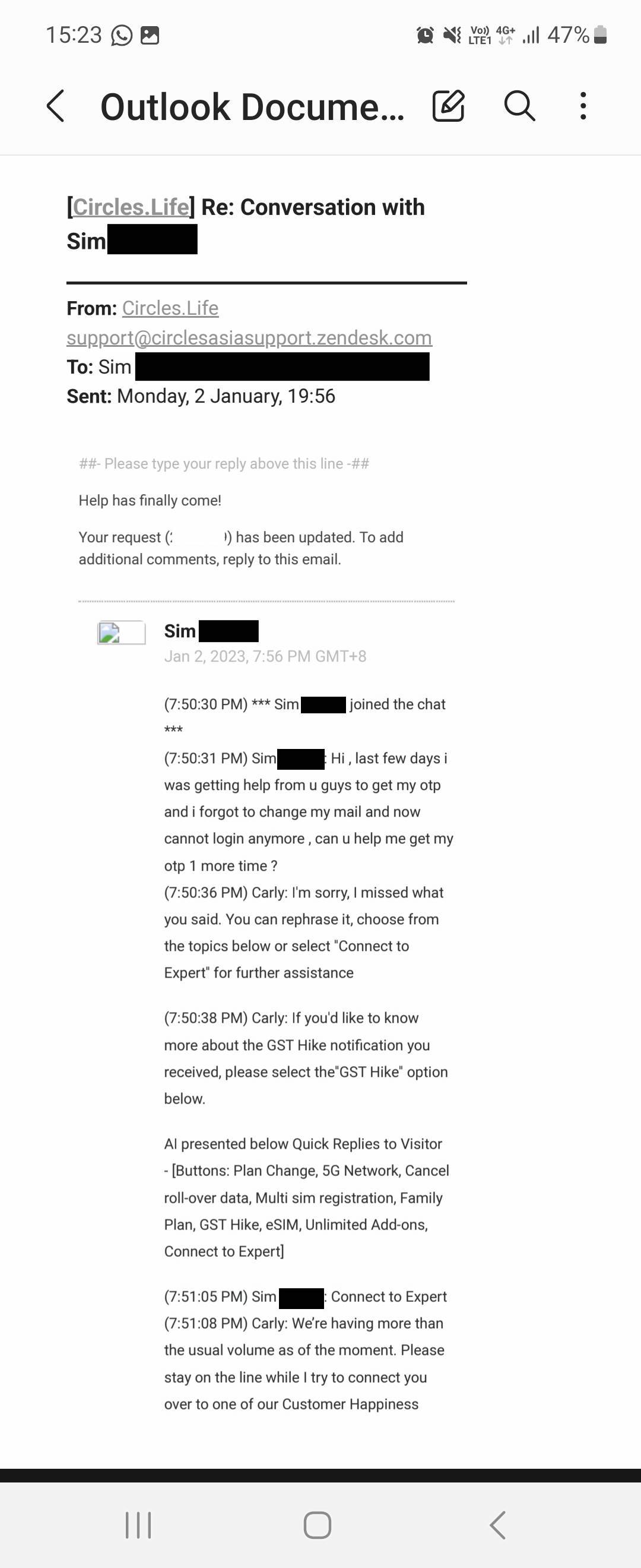
The impersonator acknowledged that they had sought help with the OTP in the "last few days", but claimed to have forgotten to "change my mail" at the time.
Again, the impersonator requested help with the OTP to resolve purported troubles with email access.
 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
Similarly, a service agent replaced the chat bot upon the impersonator's request.
The agent issued a security challenge to ensure that they are "only coordinating with the main account holder".
As like before, seemingly correct personal details were provided.
Eventually, the OTP was given to the impersonator.
 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
This time, however, the impersonator didn't stop there.
eSIM activated
At the same time Sim received the email of the chat log, she lost connection to her phone line.
The moment it dawned on her that the impersonator might have activated the eSIM, Sim attempted to contact Circles.Life.
Unfortunately, she found that their live chat service ended at 8pm that day.
Desperate, Sim's husband reached out to Circles.Life on Facebook.
Sim's phone line was eventually suspended with the help of the telco's service agent slightly more than an hour later at 9:18pm.
Attempted access to e-commerce accounts
However, it seemed to be too late.
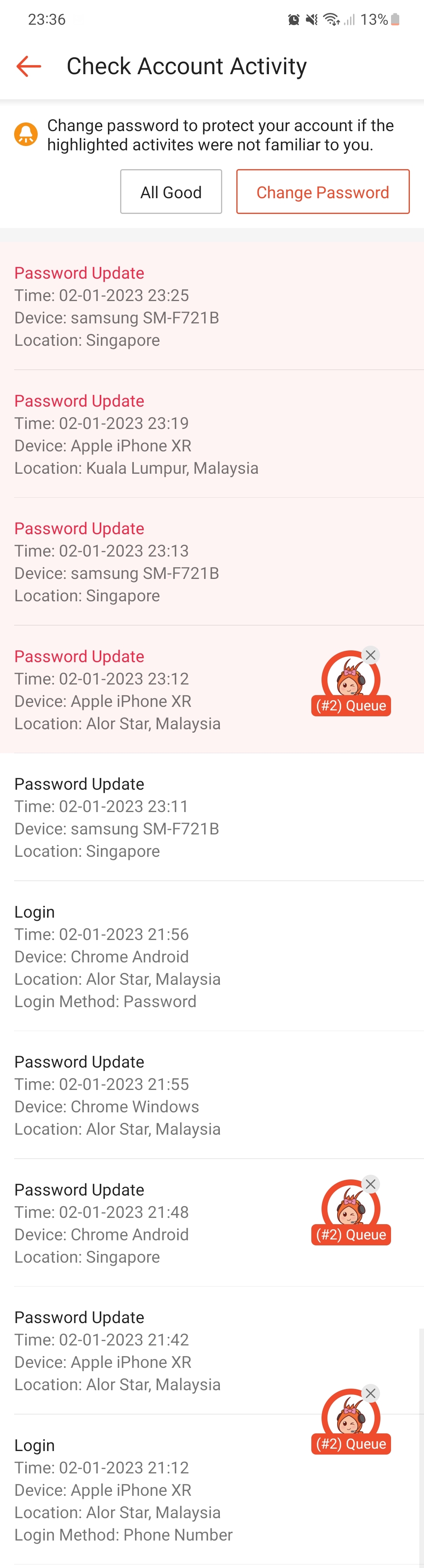
Sim shared that although she thought the line was successfully suspended, "there were actually activities going on in my Shopee account".
"As I was still in the midst of calling to cancel my various cards and suspend my bank accounts, my UOB card was still active at that point of time which allowed the hacker to top up S$500 to my Shopee Pay wallet", Sim recounted.
What ensued was a game of cat and mouse.
The impersonator attempted to make a purchase on Shopee with Sim's account.
"Then there were many attempts to lock out each other, with me using my email to reset my Shopee password and for the hacker, it could likely be using the OTP sent to my phone number to reset the password", Sim surmised.
After five failed attempts to Sim's Shopee Pin, her Shopee Pay wallet was frozen.
 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
Making contact with the malicious actor
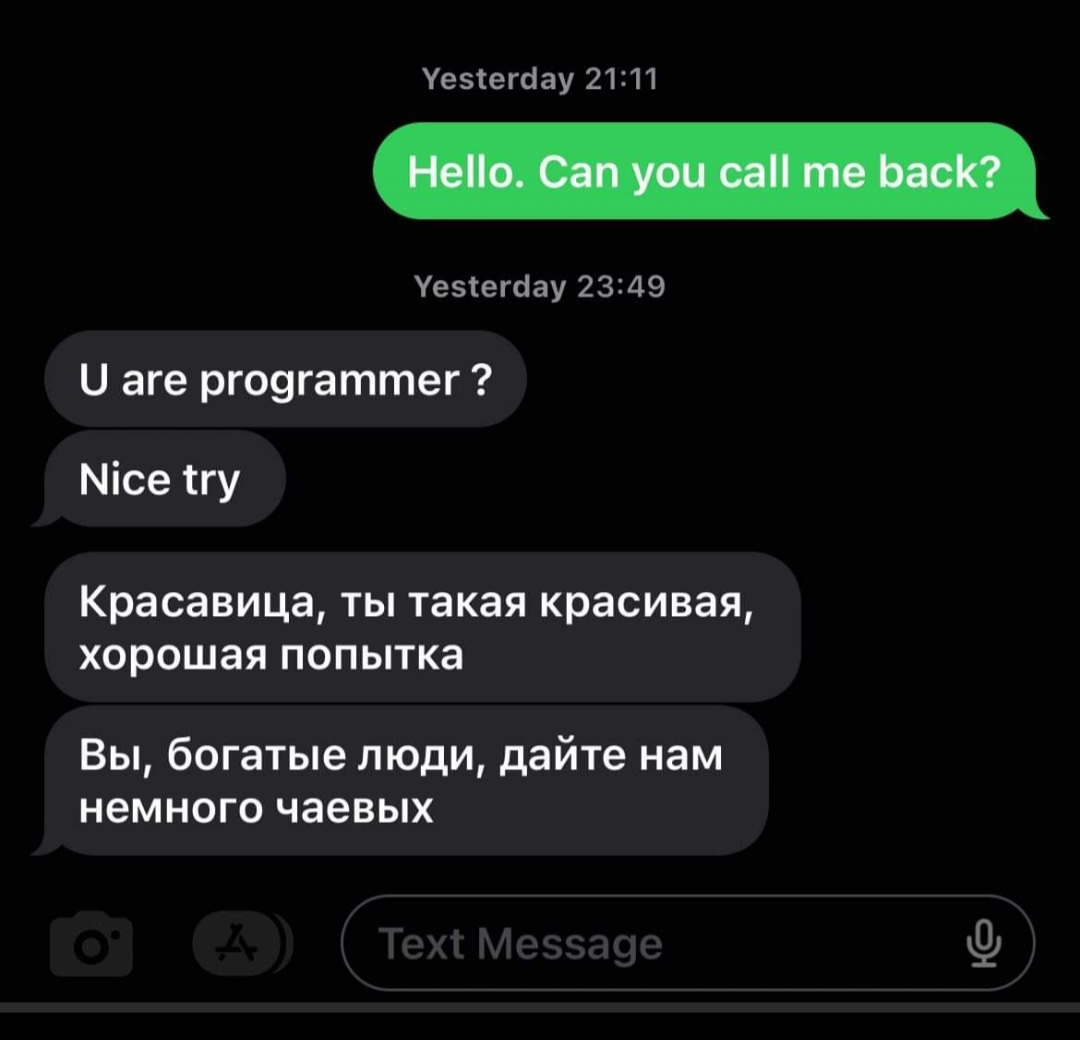
With the impersonator now in the driver's seat of Sim's phone line, Sim's husband reached out to the impersonator via Sim's phone line at 9:11pm in an attempt to reason with the bad actor.
The impersonator responded in what appears to be Cyrillic script, with a taunt and presumably a ransom demand of US$300 (S$400).
 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
The impersonator continued communicating with Sim and her husband via email.
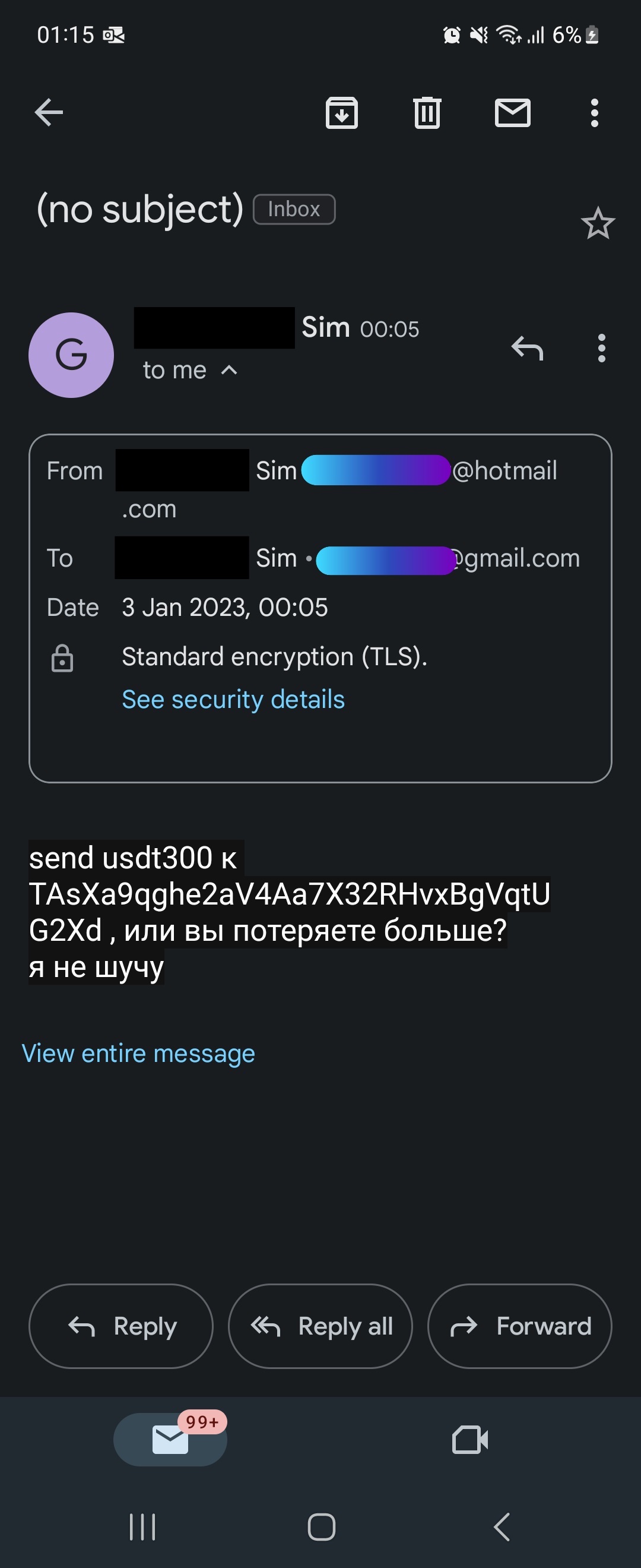 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
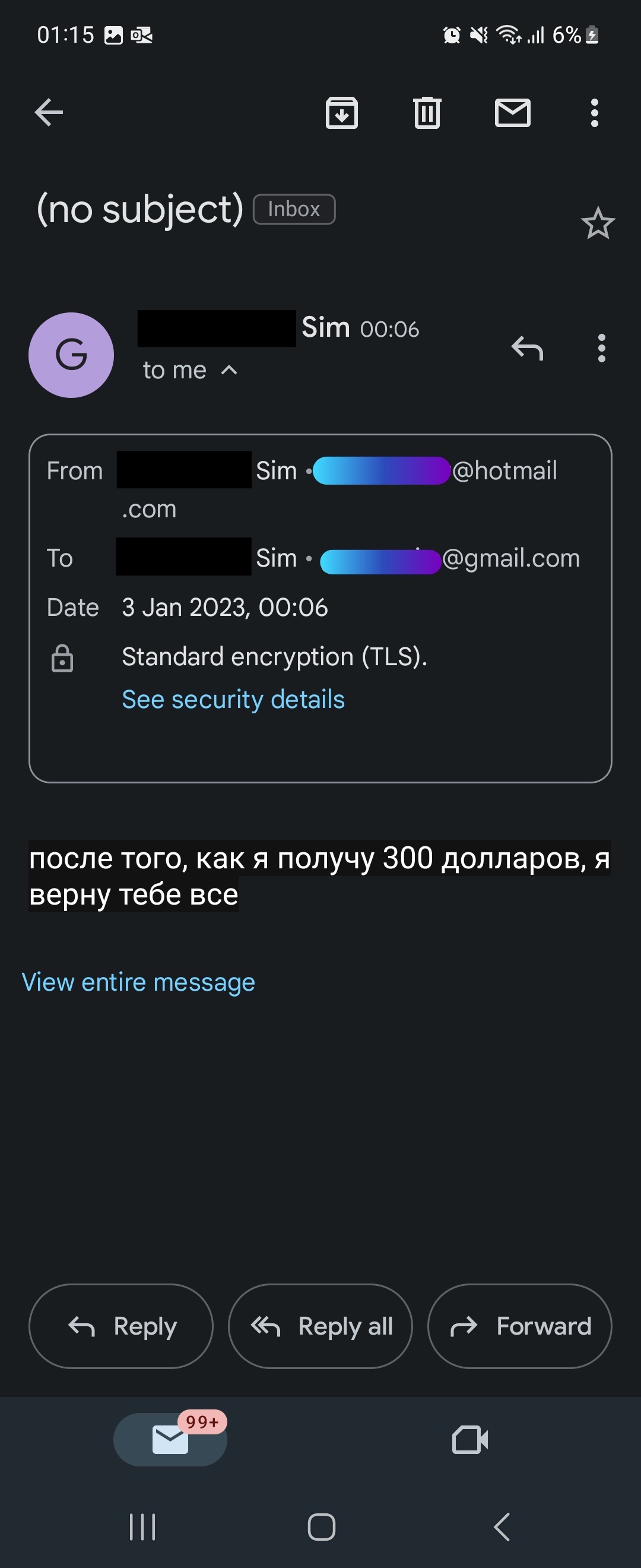 Screenshot courtesy of Sim.
Screenshot courtesy of Sim.
That same night, attempts to top up cash into Sim's Lazada account failed.
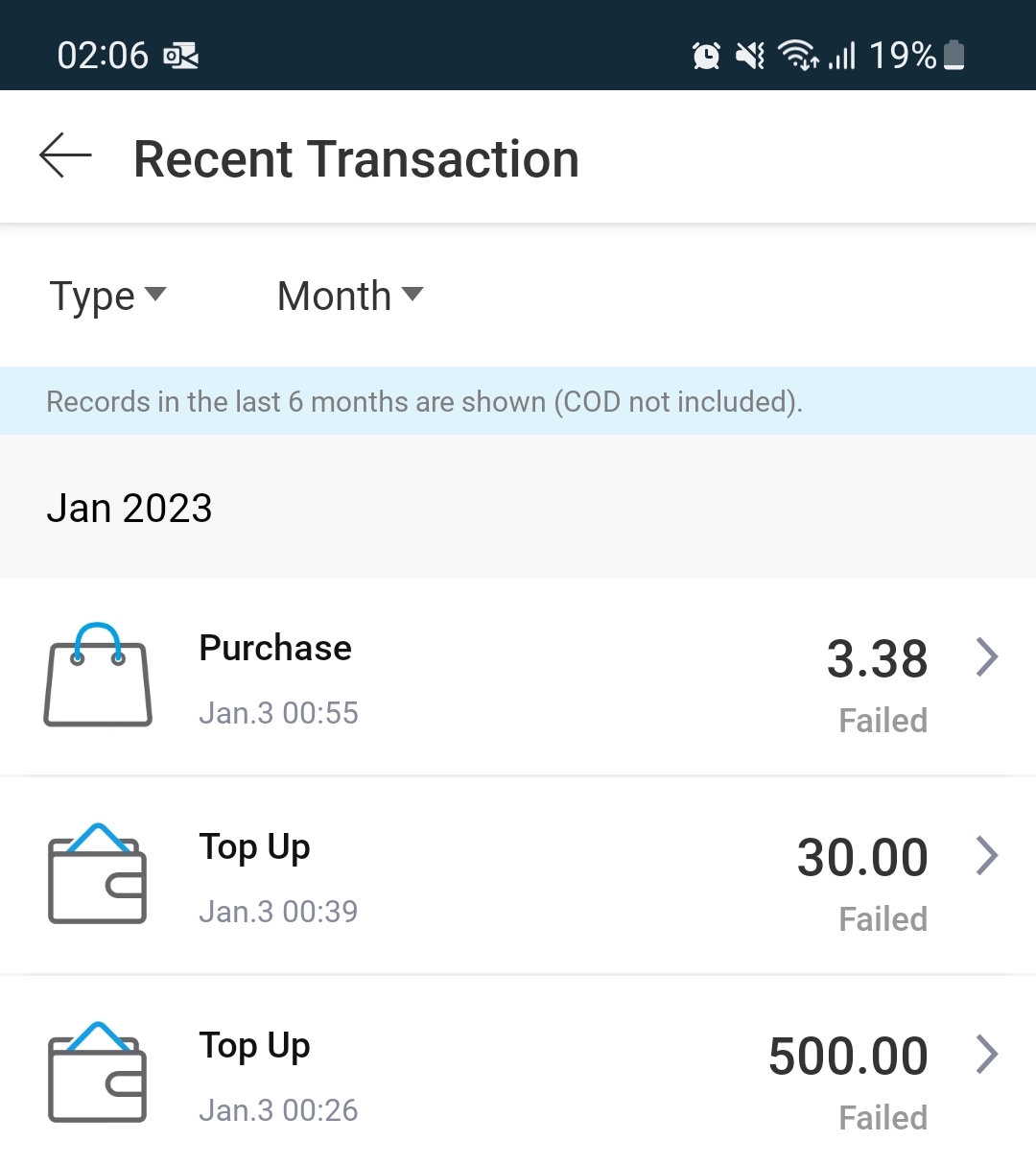
Eventually, the attempts to take over Sim's account stopped.
"I would think it stopped when all my accounts that could be overtaken by OTP were overtaken. And with my bank cards and accounts cancelled or locked, there could be no further attempt to transfer out my funds," Sim said.
Sim shared that the impersonator successfully accessed her Shopee, Lazada, Grab and PayPal accounts.
She also lost access to her emails and WhatsApp account.
Thankfully, the impersonator only managed to make off with a grand total of S$6.99 from Sim's GrabPay wallet.
Sim has no clue how the impersonator managed to gather all her personal details.
"I did ask Circles.Life if it could be an internal data breach but after their investigation, they confirmed it is not due to their internal data breach", Sim said.
Left distraught after ordeal
Following the incident, Sim shared that she had to take time away from work to deal with the aftermath of the ordeal, including giving statements to the police.
The whole episode has caused her great distress, so much so that she has had sleepless nights since the incident.
"It took Circles.Life days before acknowledging their problem and the compensation they were willing to give to me is free 12-month mobile subscription with them", Sim said.
Sim pointed out that the telco clarified that what they offered was not "compensation" but "goodwill", and she has not accepted the offer.
On Jan. 3, Sim received a replacement physical SIM card from Circles.Life to "override" the eSIM activated by the impersonator.
Before the incident, Sim had been using Circles.Life for more than a year.
She has since switched telcos, although she is keeping the Circles.Life line active for now as she makes the transition to her new phone number.
In response to queries from Mothership, the police confirmed that reports were lodged and investigations are ongoing.
Perplexed by security process
In the wake of the incident, Sim was left with several realisations and wonderings about the telco's security process.
For one, Sim feels that there could have been "protocols in place" to prevent changes to the customer's account from the moment she reported about the suspicious activity on Dec. 29.
"This should have made my account a high-risk case that would warrant their immediate attention as I did highlight to them how detrimental it could be if the 'hacker' succeeded in taking over my account", Sim opined.
From the experience, Sim also realised that she was left with little means of emergency assistance, such as a 24-hour hotline, on Jan. 2 after 8pm.
Sim guessed that the impersonator might be exploiting this fact, since the chat on Jan. 2 was initiated close to 8pm.
Crucially, Sim shared that she was later told by Circles.Life that the phone line suspension "is for outgoing calls and data usage only".
As such, the impersonator was able to receive "incoming messages nonetheless", including the OTPs, Sim speculated.
"I would think they could have fully suspended my line after I reached out to them via FB messenger", Sim wondered.
Full protection extended following incident: Circles.Life
A Circles.Life spokesperson told Mothership that the telco regards customer data safety as a "top priority".
According to the spokesperson, its in-app Live Chat function is available from Mondays to Fridays, 8am to 11pm.
It is also available on Saturdays, Sundays and Public Holidays from 8am to 8pm.
Users will also be able to "obtain timely responses" on Facebook messenger [daily from 8am to 11pm], emails and voice calls, the spokesperson added.
Speaking on the incident, the spokesperson said:
Following the incident, Circles.Life moved swiftly and decisively to extend its fullest protection before escalating the matter to the relevant authorities and support teams to resolve the matter.
We can therefore confirm the absence of any further suspicious in-account activity post-suspension following a comprehensive review process. As a result, the customer has also accepted Circles.Life's offer to reactivate the line and is in the midst of discussions regarding compensation for any inconveniences incurred. We empathise with the customer over the circumstances, and will continue to render support to the fullest extent possible.
[...]
While users are encouraged to protect their personal information via periodic reviews of their data security measures, Circles.Life also plays an active part in reminding and reinforcing its comprehensive data protection policy extending across all its users with educational materials such as regular eDMs and bite-sized social media content. More information is available here.
Mothership followed up by asking Circles.Life what their "fullest protection" entailed, and if plans to modify their security protocols, such as extending helpline hours, and the process of escalating urgent requests are being considered.
In response to these queries, the spokesperson added:
The modus operandi for scams and fraud cases are ever-evolving and we want to continuously remind the community to remain vigilant against new variations. As soon as the potential of fraud was ascertained, Circles.Life suspended the account in question as part of our damage control protocols to minimise data compromisation, while maintaining an open line of communication and support with the customer.
[...]
Following the incident, Circles.Life will be setting up a dedicated Scam & Fraud taskforce to manage future incidents of a similar nature, thus ensuring quicker response times as a result of a streamlined issues escalation process. Amidst a backdrop of evolving scams, Circles.Life will continue to work in tandem with all relevant regulatory bodies to educate users on the risks associated with personal data protection, while advising its users to remain vigilant and exercise discernment as we continue to re-assess our security protocols and issues escalation processes to safeguard our community.
Responding to queries from Mothership, an Infocomm and Media Development Authority (IMDA) spokesperson said that IMDA is currently investigating the incident.
"We are unable to share more information as investigations are ongoing", they added.
Mothership has also reached out to the Cyber Security Agency for comments, and will update the article as soon as more information is shared.
Process issue, not "hacking": Cybersecurity expert
Speaking to Mothership, Aaron Ang, Director of Education at Right-Hand Cybersecurity and Chief Executive (Cyber Youth Collective) at Cyber Youth Singapore, shared that this is not a case of "hacking" nor a matter of vulnerability.
Method used by malicious actor
Rather, the malicious actor had employed a method known in the industry as "social engineering".
Ang shared a video which helped exemplify "social engineering" and was similar to the modus operandi of the malicious actor in Sim's case.
Simply put, it involves bad actors using emotional cues to trick call centre service agents, among others, into giving access to a victim's accounts.
In the case of Sim, the malicious actor had the added advantage of Sim's personal information to trick the telco's staff:
"What’s likely to have happened is that the user’s personal details were leaked through certain means, and the perpetrator is using that info to get access to the account."
When asked if the ease of activation for eSIMs was an issue, Ang said no, although using an eSIM does "bypass certain traditional verifications that traditional telcos have".
"It’s more of a process issue rather than a vulnerability", Ang shared.
A lot of “hacks” don’t happen because hackers hack technical stuff... It happens because of lapses in policies and processes.
What went wrong with the process
Process-wise, Ang pointed out that OTPs should not be provided over chat.
"It just defeats the purpose of [having an] OTP," Ang said.
If a user reaches out to request for changes to an account, there should be "added verification", and it "can't just be over chat".
Ang provided an example of what "added verification" may look like:
One way of verification would be to use the Singpass app to verify your identity (same way you use it to log on to government websites -- scan the QR code with the SingPass app). Corporates can already make use of this service, as I’ve seen some companies do that to verify identity.
However, Ang recognised that more security checks may mean more inconvenience to the users.
For a user who may have genuinely lost their devices and do not have access to apps like Singpass, "it might add frustration".
Small but significant part users can play
When asked what users can do to protect themselves, Ang highlighted that it is incredibly easy for bad actors to gain access to one's personal identifiable information (PII).
He shared:
"Even something as simple as posting a family photo saying "the Tan family wishes all a happy new year" and tagging everyone in the picture can allow a social engineer to work his way in to get PII of someone."
What users can do is to be more aware of the importance of protecting one's personal data, such as their NRIC numbers.
"People usually think 'I’m not some big shot, so what if they have my NRIC number?'" Ang said.
However, things that may seem trivial, such as "knowing your rights when it comes to personal data", can go a long way.
Top image via Sim
If you like what you read, follow us on Facebook, Instagram, Twitter and Telegram to get the latest updates.