Follow us on Telegram for the latest updates: https://t.me/mothershipsg
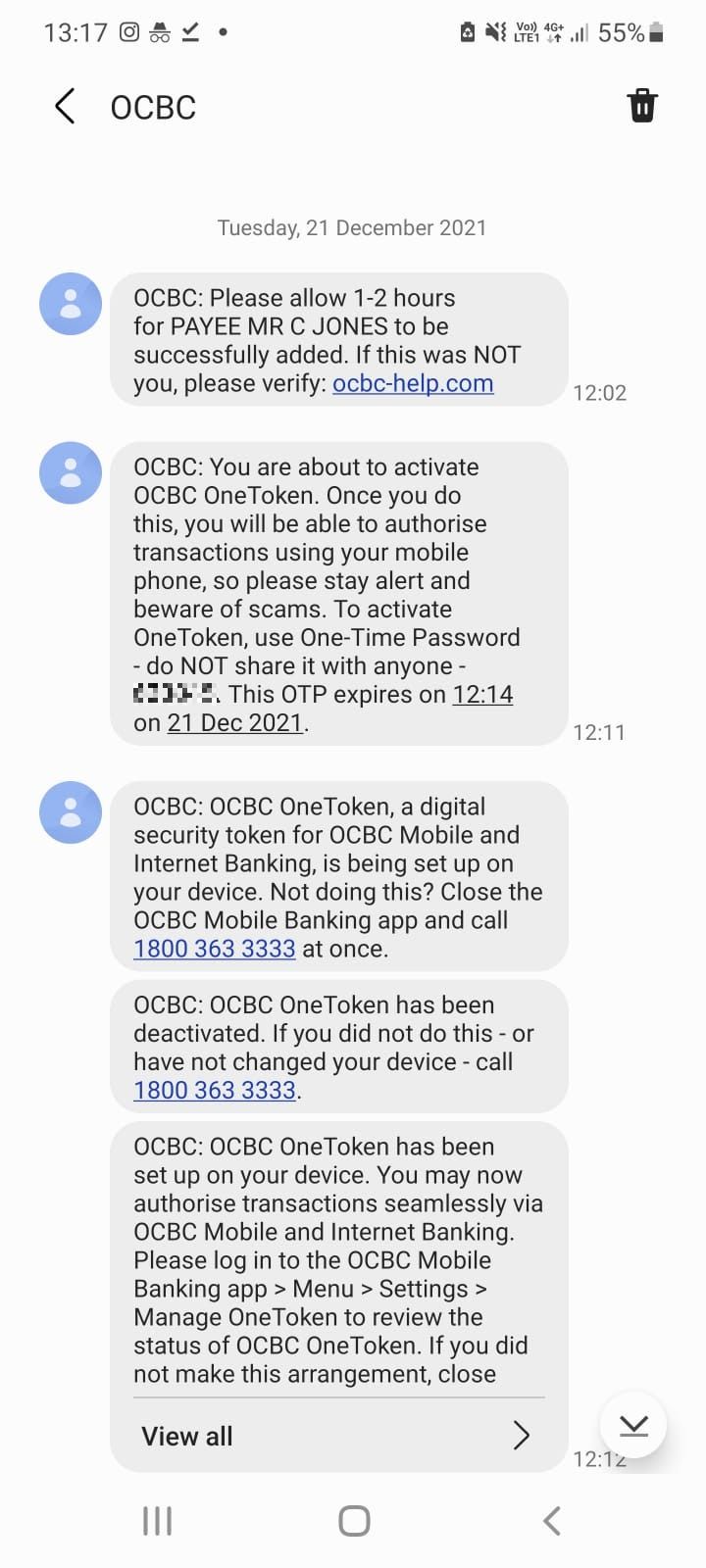
A number of Singaporeans lost their life savings in a span of a few hours in the recent OCBC phishing scam after unwittingly divulging their account details and OTPs to scammers.
Almost all of the victims who Mothership spoke to shared that they had clicked on phishing links sent via SMSes that appeared in the same thread as all the other official OCBC messages.
The victims said post-scam that they had no reason to believe that the messages in the thread were not to be trusted, given that the channel has been used to transmit authentic messages before.
 Screenshot via Mothership reader.
Screenshot via Mothership reader.
Not hard to spoof SMSes
After the SMS phishing scam became national news, one Singaporean data scientist, who goes by Captain Sinkie, or ZP Lee, shared with Mothership just how easy it is for scammers to send SMSes, with the suggestion that the authorities clamp down on such practices.
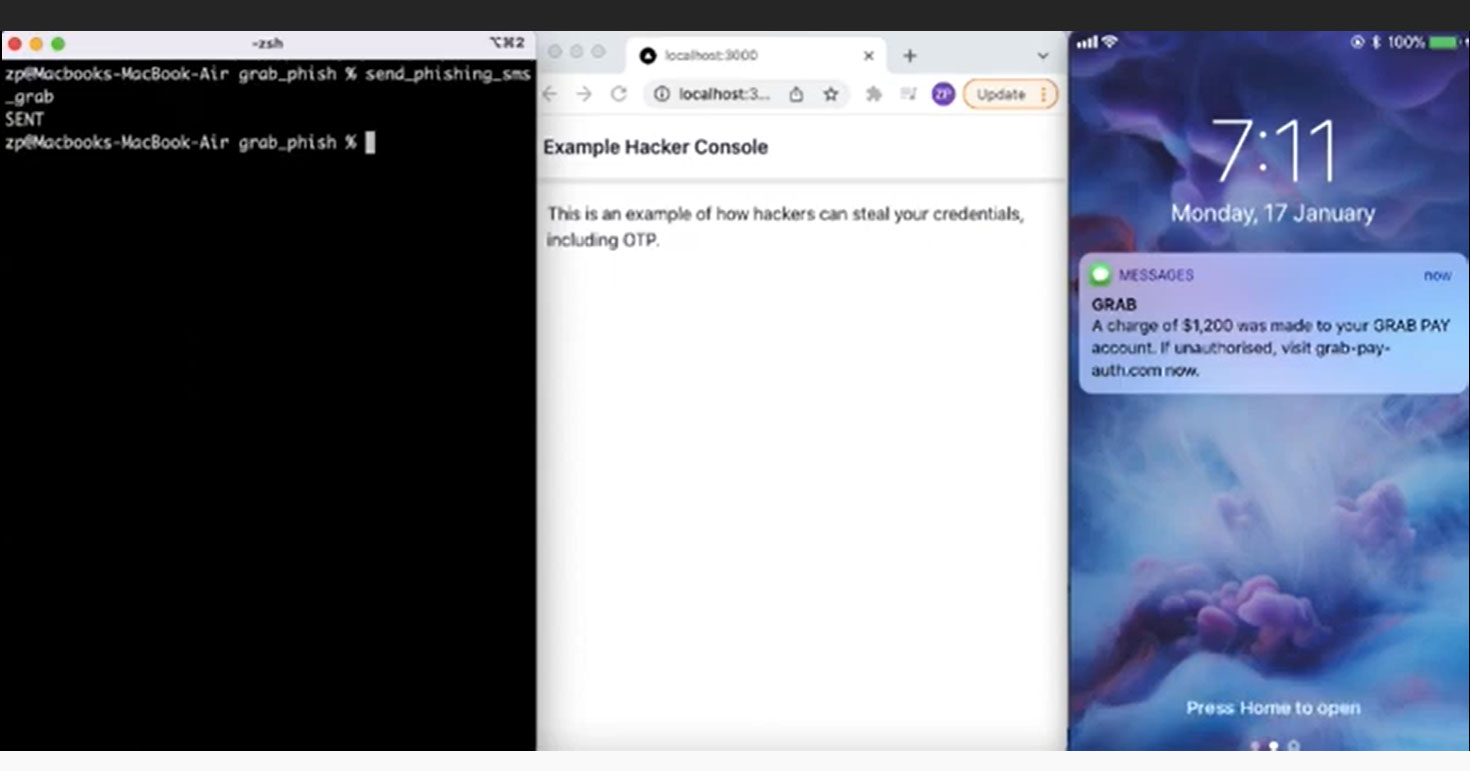
How the SMS scam works
Various organisations and banks in Singapore use sender IDs in their SMSes to customers.
This refers to the text display name that users will see at the top of their message threads.
It also indicates who the text message is from, instead of an unfamiliar phone number.
SMS protocol
Lee, 31, said the scammers were able to spoof the SMS protocol by adding a "sender ID" field on SMS services.
Users' phones will then show these messages with the modified sender IDs.
Phones are also coded to group messages by sender IDs, so the spoofed messages will appear in the same thread as previous messages sent by the official sender.
Technology not new and "extremely easy" to do
Lee, who also teaches programming classes, was curious how the scammers were able to pull off this ruse.
It only took him a couple hours of researching the Internet for him to find an SMS service that allowed him to write code and send messages with fake sender IDs to himself.
Despite thinking that it would require sophisticated technology to execute, he found it "extremely easy" to do so.
He also told Mothership that this technology is not new and would not require any special software or a lot of processing power if scammers wanted to mass send these spoofed messages out to many people at once.
Managed to spoof messages from DBS, SAF, Grab and more
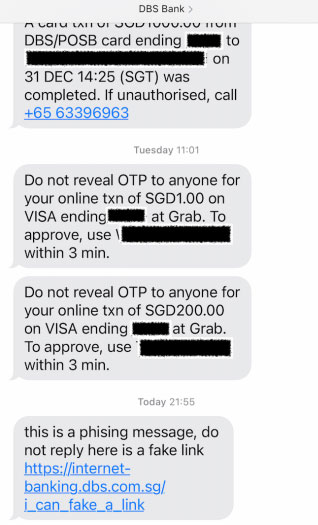
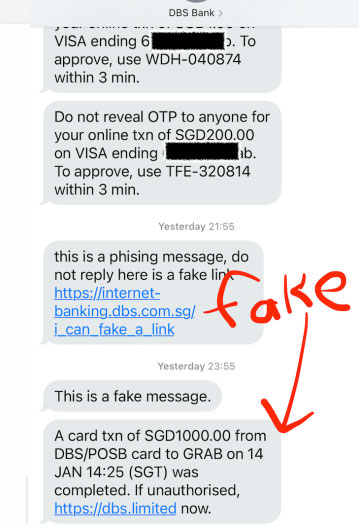
Documenting his experiments, Captain Sinkie said he managed to spoof messages from DBS Bank, warning that OCBC is not the only bank or organisation that is vulnerable to these sorts of SMS scams.
This was the message he managed to send to his own phone number:
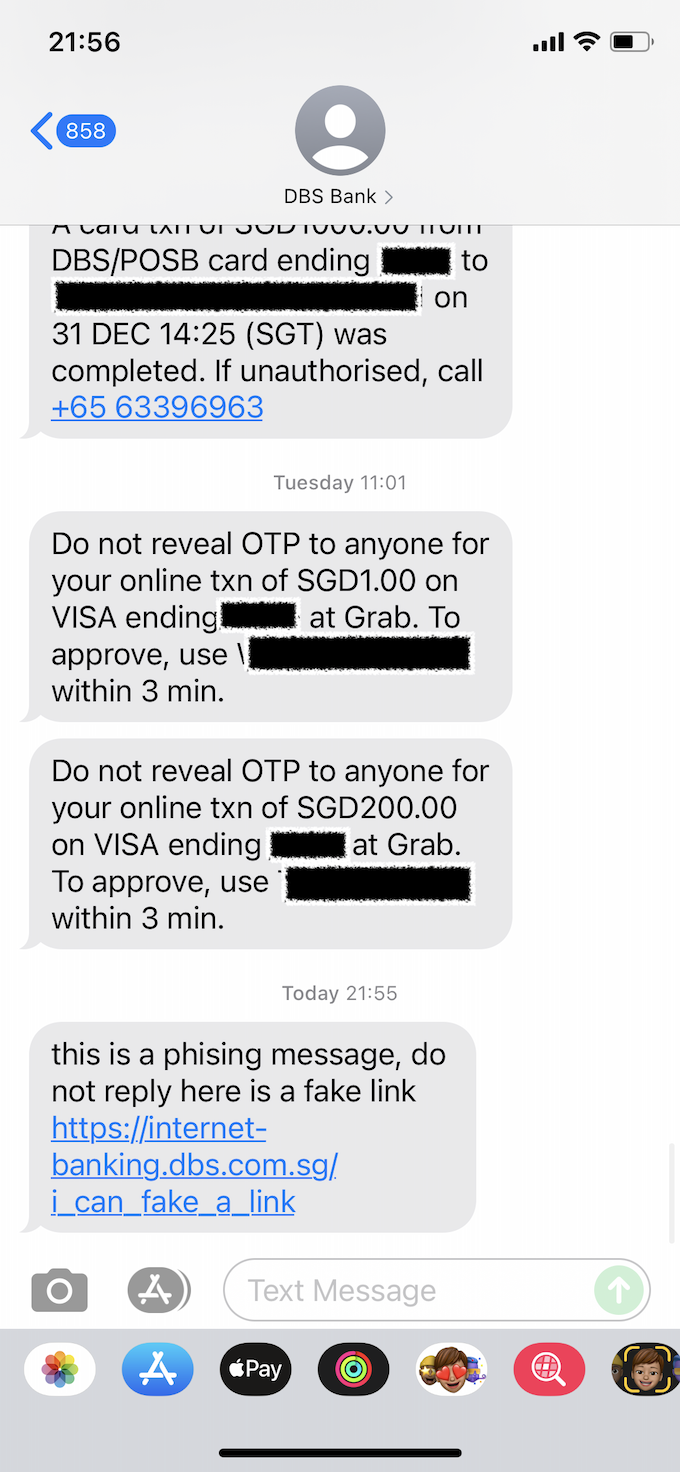 Photo via Captain Sinkie.
Photo via Captain Sinkie.
His fake message appeared together with his previous legitimate messages from DBS Bank.
He said he has alerted DBS of his findings.
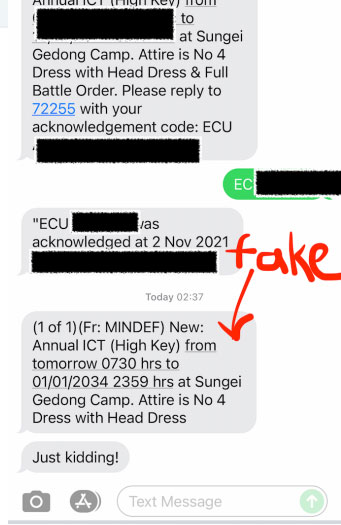
He even managed to spoof messages from "72255", the number that SAF sends out reservist reminders from.
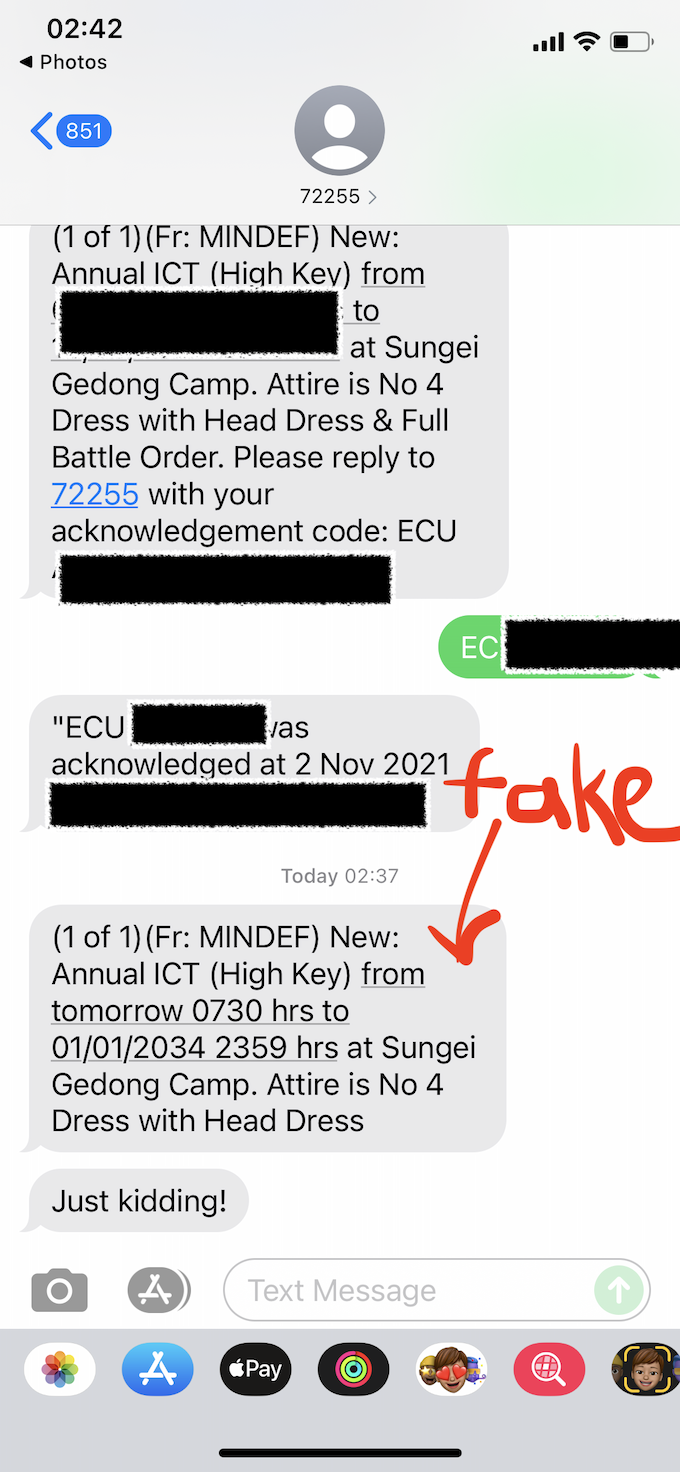 Photo via Captain Sinkie.
Photo via Captain Sinkie.
He said he was also able to do the same for other companies, such as Grab, and government agencies like the Inland Revenue Authority of Singapore (IRAS), the Ministry of Health (MOH) and the Ministry of Defence (MINDEF).
Steps taken to prevent spoofing
However, since his initial blog post went viral, most of these organisations have blocked spoofed SMSes from being sent using their sender IDs.
He was also unable to spoof OCBC's messages, presumably because authorities had blacklisted the spoofed sender IDs after multiple reports of the phishing scams emerged.
Petition for IMDA to enforce SMS sender pre-registration
Upon further research, Lee found out that certain countries require pre-registration for organisations to be allowed to send custom sender IDs.
Currently, Singapore does not have this regulation.
According to Twilio, one of the major communications companies that help businesses send messages with custom sender IDs, 51 countries require pre-registration to send out custom sender IDs.
Some countries, such as South Korea and the United States, have also banned custom sender IDs from being sent out completely.
Lee has since started a petition appealing for the Infocomm Media Development Authority (IMDA) to regulate and enforce pre-registration for sender IDs in Singapore.
 Screeenshot via Change.org.
Screeenshot via Change.org.
Doing so, he said, would help to guard against SMS spoofing scams.
At the time of writing, the petition has garnered almost 1,300 signatures.
IMDA urges more businesses to sign up for anti-SMS spoofing registry, but it might not be enough
IMDA published a forum letter in The Straits Times on Jan. 17 urging more businesses to sign up for its SMS sender ID registry pilot in light of the recent phishing scams.
IMDA said it had launched the Singapore SMS SenderID protection registry pilot in August 2021 together with the Monetary Authority of Singapore (MAS).
ST confirmed that OCBC had already signed up for the pilot, but the bank did not specify when it did so or if it was only after the recent highly-publicised scams affecting the bank's customers.
However, while Lee acknowledged that this pilot is a "good step forward", his opinion is that it is not a foolproof method for guarding against spoofed SMSes.
This is because it requires companies to proactively register for its use.
"Companies who have not registered are still vulnerable to targets of phishing scams, such is the case of the OCBC attack," said Lee.
He added that the approach also requires IMDA to actively blacklist certain SMS sender names from use.
"Scammers can still creatively come up with new phishing names to dupe potential victims. Scammer could use names like POLIS, SOS, WIFE, SGPAYNOW, etc. As long as these names are not registered by companies, hackers are still able to come up with authentic looking phishing messages to scam money. This also means that we are always on the backfoot when it comes to dealing with the SMS phishing scams," he said.
Lee's petition hopes to address this by urging the government to consider using a "whitelist" approach.
This would effectively block all sender IDs from being changed by a third party.
Instead, it would require companies to register for certain sender names before they can be used to send SMSes.
Scammers would be unable to spoof SMS sender IDs using this method.
Though spoofed SMSes are just one way that scammers can deceive people into divulging personal details, Lee hopes that requiring sender ID registration would put an end to similar SMS scams in the future:
"Already, 51 countries around the world require a registration process before specific sender names can be used. Many more countries such as US and UK outright block sender names from being used. I think it is a fair and logical solution. Too many Singaporeans have lost their hard earned savings and we should work together to stop this."
Just one part of the problem
Lee warned, however, that Singaporeans still need to be wary when it comes to entering any details on phishing websites.
"Even if the SMSes look very legit, hackers will still need to redirect you to a phishing website to steal information," he said.
He said there is still a pressing need for Singaporeans to build awareness of phishing attempts, and to be able to identify suspicious phishing links.
Follow and listen to our podcast here
Top photos via Captain Sinkie.
If you like what you read, follow us on Facebook, Instagram, Twitter and Telegram to get the latest updates.