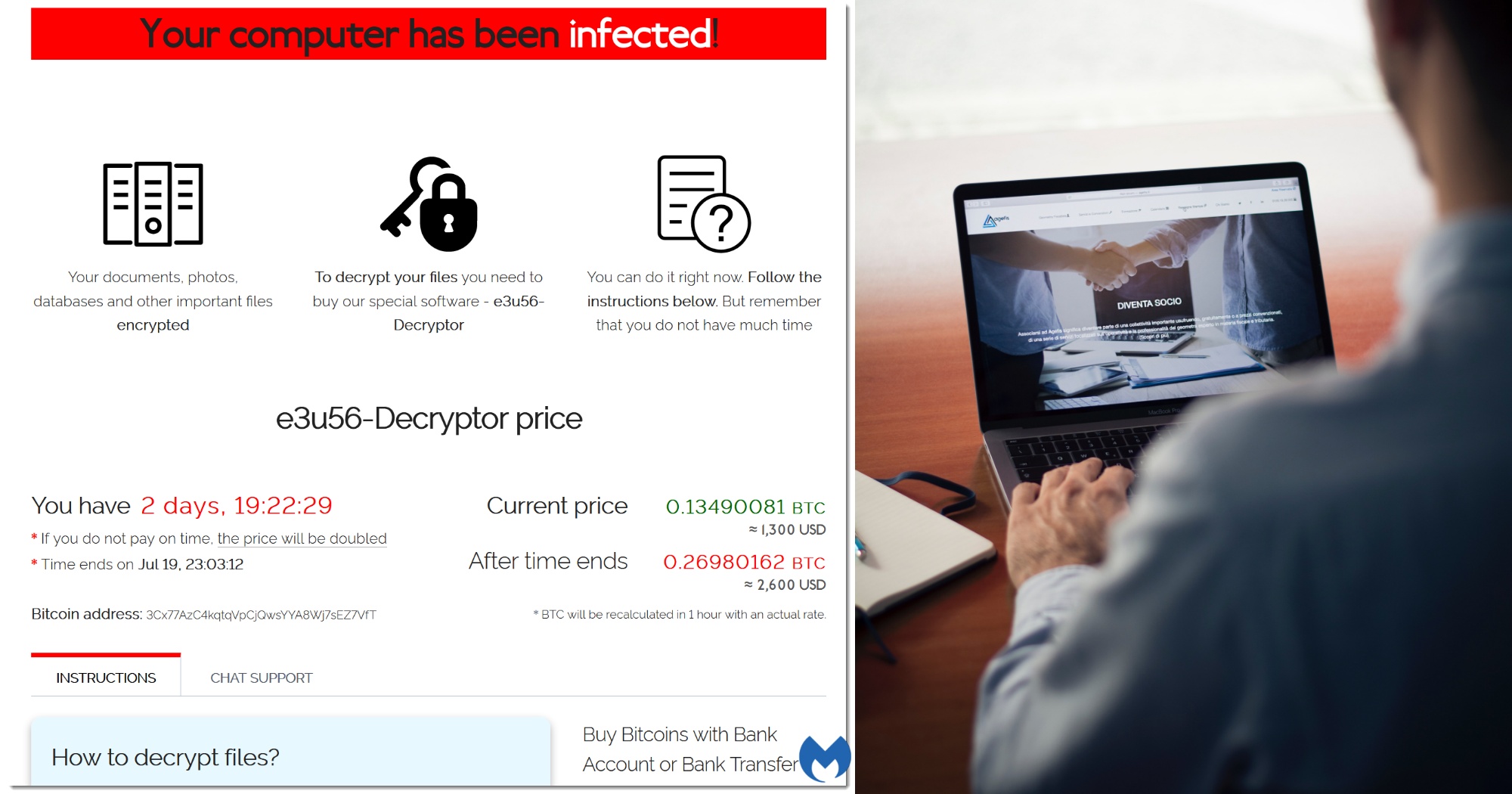
Cases of ransomware attacks are on the rise.
89 cases of ransomware attacks were reported to the Cyber Security Agency of Singapore (CSA) in 2020, a 154 per cent increase from 2019.
Ransomware is a type of malicious software that infects a computer and restricts users' access to it until a ransom is paid to unlock it.
The CSA also pointed out several observations about local ransomware attacks in its Singapore Cyber Landscape 2020 publication.
Cybercriminals appear to be fishing for larger victims in the manufacturing, retail and healthcare sectors for bigger payouts.
Those who want to utilise ransomware, but are not technologically adept, are able to get their hands on sophisticated ransomware, which is increasingly being offered as a service. This makes it easier for more criminals to get their hands on malware.
The average cost to a business in ransomware payments is US$220,000 (S$295,896) according to Coveware. So what can businesses do to protect themselves against ransomware? Local cybersecurity consulting firm INTfinity Consulting has some practical tips and real life examples to offer.
Tip 1: Use strong passwords and multi-factor authentication
This extremely simple step cannot be overemphasised.
What does a strong password look like? It’s definitely not <password123>
Key aspects of a strong password include length (longer passwords tend to be harder to hack), a mix of upper and lower case letters, numbers and symbols, and unpredictability (meaning no personal information like your name or birth date, and no dictionary words).
A strong password could look like <Cg@yhetDu239!%HHufR>. Using a password manager will also make it easier to maintain secure and unique passwords for different websites and platforms.
These make your password harder to guess with a brute-force attack. In addition, should your password somehow be disclosed, having multi-factor authentication could prevent an attacker from fully compromising your account.
Company A, a medium-sized business which operates a network that is used as a control centre to manage distributed services island-wide, was attacked because of a weak password.
The company had a misconfiguration which exposed one of its servers to the internet and allowed anyone to access it remotely.
Unfortunately, the password that guarded access to the server was too easy to guess and soon an attacker managed to enter Company A's server, and from there, access more systems within the network, allowing the attacker to get information like which account had administrative access.
The system did throw up several warning signs, like malware alerts, but no one heeded them.
Eventually the attacker managed to gain control of the administrative account within the network that gave them full control over all systems.
Using those credentials, the attacker accessed the file and email server, where they proceeded to disable scheduled backups, erase previous backups, and deployed a ransomware encryption software that crippled nearly all their systems. As a result of this, Company A had an operational downtime of more than a month.
Tip 2: Get a professional to review your website/network/database periodically
Just like how you would go for regular medical check ups for your health, it is a good practice to perform a security review on your website, network, or database regularly to spot weak areas that can be exploited.
Many Singapore-based cybersecurity companies, such as INTfinity Consulting, can do an assessment each time you implement a website change or on a periodic basis.
These assessments can range from basic essentials like gap analysis and vulnerability assessment to more comprehensive services like threat hunting and digital forensics incident response.
 Get a cybersecurity firm to assess your company’s network vulnerabilities regularly so that you can spot and fix gaps quickly. Image by Michael Geiger on Unsplash
Get a cybersecurity firm to assess your company’s network vulnerabilities regularly so that you can spot and fix gaps quickly. Image by Michael Geiger on Unsplash
Company B, which runs a bustling e-commerce business, is fully reliant on its website to market its products. And so it frequently upgrades the look of its website to attract more customers.
Unfortunately, one of its upgrades included a coding flaw which was exploited by an attacker. The attacker then went on to uncover more passwords inside the web server and finally gained access to Company B’s clients’ personal information, which could be sold on the black market.
The attacker took out the data slowly over a period of time so as not to trigger any detection mechanism. Finally, the attacker unleashed a ransomware which encrypted the data on Company B’s server.
Company B was forced to take its website offline and could only recover its e-commerce business several weeks later.
Tip 3: Update your peripheral devices like firewalls, printers, and VPN
An increasing number of organisations are deploying firewalls and VPNs (virtual private networks) as more of their employees start working from home.
However, the patches and security updates for these devices are often overlooked, sometimes for years, and this makes them prime targets for cyberattacks.
While most endpoint operating systems do a good job of enabling and pushing updates, users typically overlook peripheral devices such as printers (yes, printers can be hacked!), VPNs, and firewalls.
 You see a printer, hackers see a backdoor. Photo by Mahrous Houses on Unsplash
You see a printer, hackers see a backdoor. Photo by Mahrous Houses on Unsplash
These devices reside in the same network as your users and should be updated as frequently as your operating system.
According to INTfinity Consulting, as of July 2021, there are around 100 Singapore IP addresses that still exhibit a particular vulnerability which could have been patched more than two years ago.
Using an unpatched firewall makes your network more vulnerable because cyber threats are constantly evolving.
Once a cybercriminal bypasses your firewall and enters your network, they typically wait until they find an opportunity to access accounts with higher privileges, such as an administrator account. This will then grant them the ability to deploy their ransomware.
INTfinity Consulting also revealed that there is an increasing trend of ransomware operators misappropriating a software called Cobalt Strike.
While Cobalt Strike is marketed as a legitimate commercial software which emulates cybersecurity threats for testers to identify vulnerabilities, it has been adapted by cybercriminals to attack, extract data, and unleash malware on their victims. It is favoured by them because it leaves fewer traces of digital evidence behind, making it difficult for incident responders to track and deploy fixes.
Tip 4: Backup your data
INTfinity Consulting has this advice for backing up your data: Follow the 3-2-1 backup rule, which will be very helpful when it comes to disaster recovery.
Have three copies of your data (one copy is production data while the other two are backup copies).
Store your data on two different media, and make sure that at least one copy is located offline or even better, off-site.
Back up often and always make sure that backups can be restored.
Tip 5: Be vigilant against phishing emails
Lastly, ransomware is commonly delivered through phishing emails where users are lured into clicking a malicious download link or opening a seemingly innocuous email attachment.
Staff should be taught to identify suspicious emails, especially those that originate from outside the organisation.
 Don’t want to fall victim to a ransomware attack? Keep your data backed up offline and make sure you are extra vigilant about emails that come from outside the company. Photo by Priscilla Du Preez on Unsplash.
Don’t want to fall victim to a ransomware attack? Keep your data backed up offline and make sure you are extra vigilant about emails that come from outside the company. Photo by Priscilla Du Preez on Unsplash.
For this purpose, INTfinity Consulting suggests filtering emails that originate from external senders and adding “[External]” to the subject. This is to prompt staff to be more vigilant when they open the email.
For more information on INTfinity Consulting and the services it provides, you can head over to its website here.
Thanks to this article that was sponsored by INTfinity Consulting, this writer went to change all his passwords. Top images via Agefis on Unsplash, malwarebytes.com
If you like what you read, follow us on Facebook, Instagram, Twitter and Telegram to get the latest updates.