SingCert warns of ‘ongoing phishing campaign’ targeting those hit by global IT outage by offering help
Examples include phishing emails and calls impersonating CrowdStrike support.
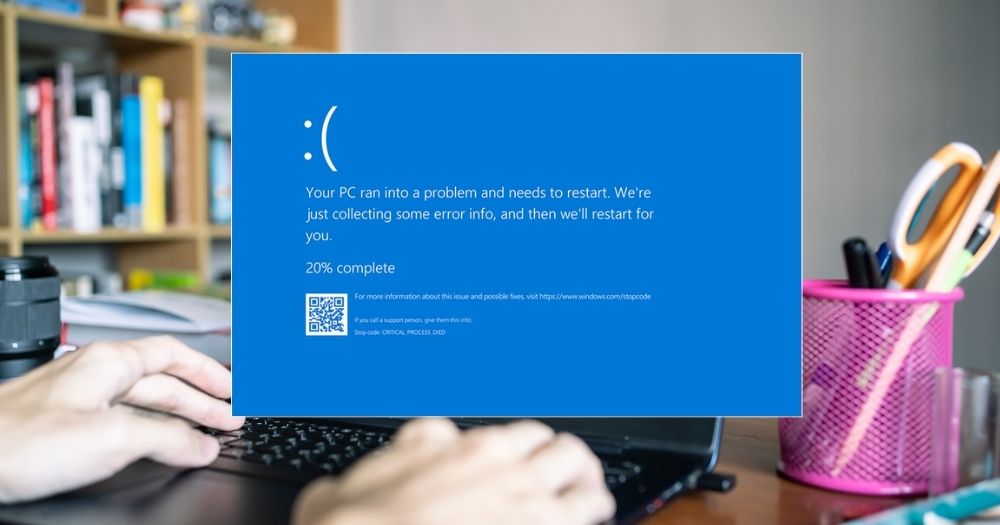
In the wake of the global IT outage triggered by cybersecurity firm CrowdStrike's update, reports have surfaced detailing an ongoing phishing campaign targeting CrowdStrike users.
Threat actors have capitalised on the outage to execute various deceptive activities, the Singapore Cyber Emergency Response Team (SingCert) shared in an advisory.
Phishing activities
The various phishing activities include:
- Sending phishing emails posing as CrowdStrike support to customers
- Impersonating CrowdStrike staff in phone calls
- Posing as independent researchers, claiming to have evidence that the technical issue is linked to a cyberattack and offering remediation insights
- Selling scripts purporting to automate recovery from the content update issue
Possible malicious domains associated with the ongoing campaign, impersonating CrowdStrike’s brand, were also identified and listed in the advisory.
The list included entries such as "crowdstrikebluescreen[.]com", "crowdstrike-bsod[.]com" and "crowdstrikeupdate[.]com".
"System administrators may wish to configure their firewall rules to block connections to the following domains associated with the campaign," SingCert stated.
SingCert advised organisations to ensure they are communicating with CrowdStrike representatives through official channels and adhere to technical guidance the CrowdStrike support teams have provided.
Fixing blue screen of death errors
The global IT outage also saw widespread reports of blue screen of death (BSOD) errors on Windows hosts.
BSOD is commonly used to describe a system crash on Microsoft's Windows operating system.
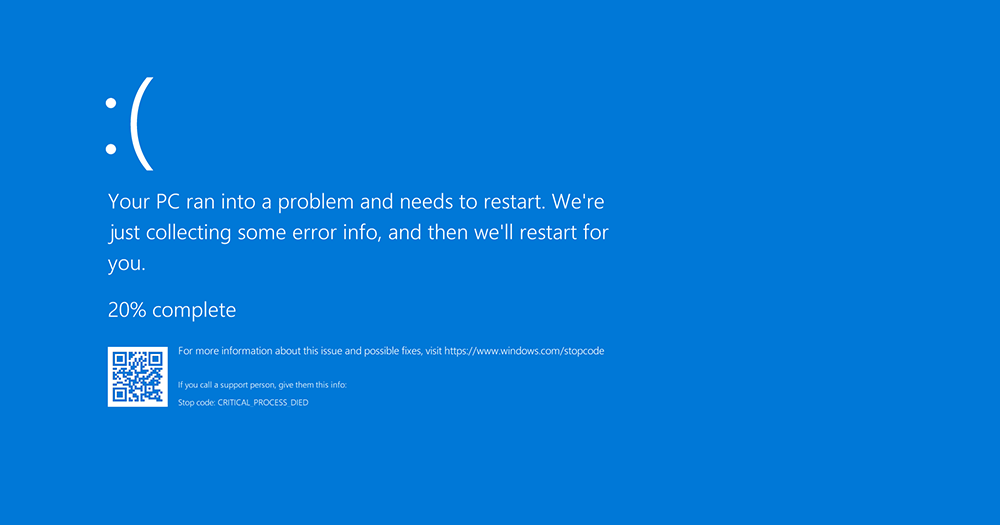 Photo from Wikipedia
Photo from Wikipedia
For those using the affected systems, SingCert has also issued an advisory outlining steps to mitigate the impact.
SingCert advisory
Users and administrators of affected systems can take the following steps to circumvent the error:
1. Boot Windows into Safe Mode or the Windows Recovery Environment.
2. Navigate to the C:\Windows\System32\drivers\CrowdStrike directory.
3. Locate the file matching the pattern "C-00000291*.sys" and delete it.
4. Boot the host normally.
Users and administrators of affected systems within a public cloud or similar environment (including virtual) can take the following steps:
1. Detach the operating system disk volume from the impacted virtual server
2. Create a snapshot or backup of the disk volume before proceeding further as a precaution against unintended changes
3. Attach/mount the volume to a new virtual server
4. Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory
5. Locate the file matching “C-00000291*.sys” and delete it.
6. Detach the volume from the new virtual server
7. Reattach the fixed volume to the impacted virtual server
Alternatively, you can roll back to a snapshot taken before 0409 Coordinated Universal Time (UTC) — reverting a disk to a previous version before the error.
Users can also visit CrowdStrike's support portal for the latest information and recommendations.
Services restored for most companies
Most companies in Singapore affected by the global IT outage have restored their services to the public as of 6 am on Jul. 20.
The Ministry of Digital Development and Information (MDDI) said in a press release that these include airline check-in services, newspapers, radio, and postal services.
The ministry added that they are closely monitoring the situation and will provide assistance to the companies if required.
Related stories
Top photos from Canva and Wikipedia
MORE STORIES




















